| Home Prev |  NetWall 6000 Series Getting Started Guide NetWall 6000 Series Getting Started Guide
|
Next |
|---|
This chapter discusses initial cOS Core configuration for the 6000 Series. The initial setup sections consist of:
Section 4.1, Web Interface and Wizard Setup describes using a web browser with the cOS Core Setup Wizard over a network connection.
Section 4.2, Manual Web Interface Setup describes using a web browser over a network connection to perform setup manually (without the wizard).
Section 4.3, Manual CLI Setup describes manual setup using the cOS Core CLI either over an SSH network connection or directly through a local console connection to cOS Core.
In all the above cases, it is assumed that the requirement is to set up cOS Core so that traffic from a protected network can enter one firewall Ethernet interface, be filtered, and then exit another Ethernet interface towards the Internet or other wide area network.
![[Tip]](images/tip.png) |
Tip: Upgrade to the latest cOS Core version |
|---|---|
|
A new NetWall 6000 Series unit may not have the very latest cOS Core version pre-installed. After initial setup, it is recommended to upgrade to the latest available cOS Core version. The procedure for upgrading is described in the separate cOS Core Administration Guide. |
This section describes the setup when accessing cOS Core for the first time through a web browser. The cOS Core user interface accessed in this way is called the Web Interface (or WebUI). It is assumed that a physical network connection has been set up from a management computer to the default management Ethernet interface (described in Section 3.4, Management Computer Connection).
![[Note]](images/note.png) |
Note: Some screenshots have been rearranged |
|---|---|
|
Some of the screenshot images in this section have been rearranged to better fit the page size. However, all relevant details in the images have been preserved. |
Connect to cOS Core By Browsing to https://192.168.1.1
Using a modern web browser, enter the address https://192.168.1.1 into the navigation window.
![[Note]](images/note.png) |
Note: HTTP access is disabled |
|---|---|
|
HTTP management access is disabled in the default cOS Core configuration and HTTPS must be used. Unencrypted HTTP access can be enabled by the administrator but this is not recommended. |
Troubleshooting
If there is no response from cOS Core and the reason is not clear, refer to the checklist in Section 4.6, Setup Troubleshooting .![[Important]](images/important.png) |
Important: Do not access cOS Core via a proxy server |
|---|---|
|
Make sure the web browser doesn't have a proxy server configured for the cOS Core management IP address. |
The cOS Core Self-signed Certificate
When responding to the first https:// request in a browser session, cOS Core will send a self-signed certificate to the browser. Browsers will automatically flag this self-signed certificate as posing a potential security risk. For example, the following message might be displayed by the browser.
The browser should now be told to accept the Clavister certificate to continue.
![[Note]](images/note.png) |
Note: Sending a CA signed certificate can be configured |
|---|---|
|
It is possible to configure cOS Core to use a CA signed certificate instead of its default self-signed certificate for the management login. Doing this is described in the cOS Core Administration Guide. |
The Login Dialog
cOS Core will next respond with the initial login dialog page, as shown below.
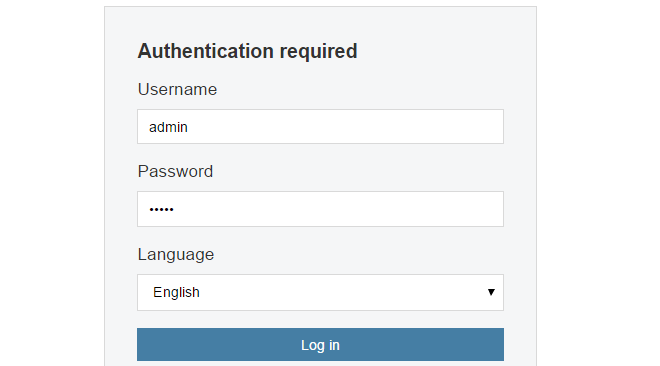
The available Web Interface language options are selectable at the bottom of this dialog. This defaults to the language set for the browser if cOS Core supports that language.
Enter the default administrator username credentials of username admin and password admin.
Starting the Setup Wizard
After logging in for the first time, the cOS Core Web Interface will appear and the cOS Core setup wizard will begin automatically in a popup window. If the wizard is blocked by the browser, it can be started manually by pressing the Setup Wizard button in the Web Interface toolbar (shown below).
Once the wizard is started, the first dialog displayed is the wizard welcome screen.
Canceling the Wizard
The setup wizard can be canceled at any point before the final Activate screen. It can be run again by pressing the Setup Wizard button in the Web Interface toolbar. Once any configuration changes have been made and activated, either through the wizard, Web Interface or CLI, then the wizard cannot be run since this requires that cOS Core has its factory defaults.The Wizard Assumes Internet Access Is Possible
The wizard assumes that Internet access will be configured. If this is not the case, for example if the firewall is being used in Transparent Mode between two internal networks, then the configuration setup is best done using the manual Web Interface steps or through the CLI instead and these methods are explained in subsequent sections.Advantages of the Wizard
The wizard makes setup easier because it automates what would otherwise be a more complex set of individual setup steps. It also reminds the administrator to perform important tasks such as setting the date and time and configuring a log server.The steps that the wizard goes through following the welcome screen are listed next.
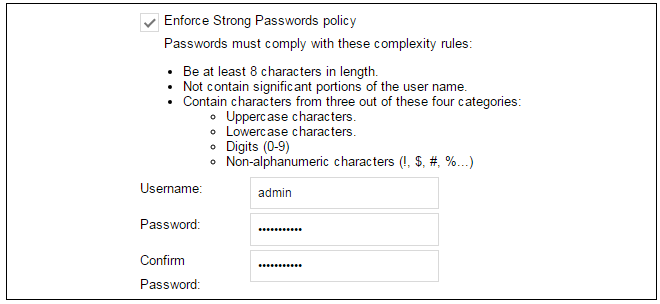
Wizard step 1: Enter a new admin password and optionally change the username
The first step in setup with the wizard is to enter a new password for the admin user. The admin username can also be changed if required, as shown in the screenshot below.The Enforce Strong Passwords option is present in cOS Core versions from 11.05 onwards. This is a global setting that will enforce the listed strong passwords rules for all users in any local user database in the configuration. If required, this option can be disabled later. However, it is recommended to leave this option enabled, which means that the default admin password must be changed to a conforming strong password before the wizard can move on to the next step.
Note that restoring cOS Core to factory defaults will restore the original admin/admin credential combination for management access.
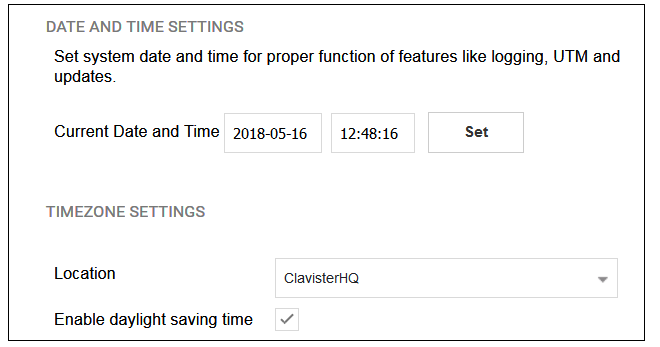
Wizard step 2: Set the date and time
Many cOS Core functions rely on an accurate date and time, so it is important that this is set correctly in the fields shown below. The default time zone location is ClavisterHQ which means the default location and time zone will be Stockholm. If this is not correct it should be changed to another location and timezone using the drop-down list.
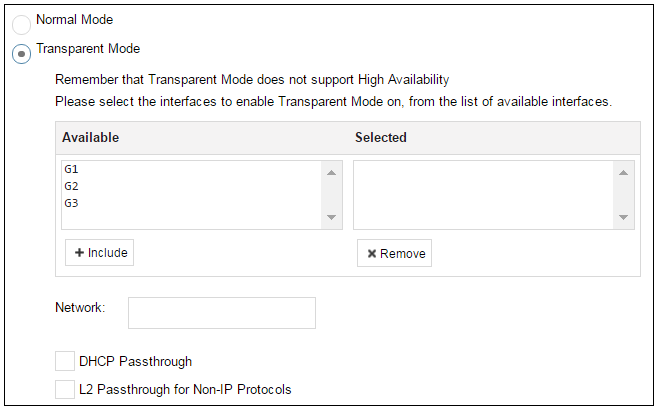
Wizard step 3: Select transparent mode interfaces
This step allows any transparent mode interfaces to be set up. If no transparent mode interfaces are required, leave this dialog in the default Normal Mode and go to the next step. Transparent mode interfaces can be configured at any time later, outside of the wizard.
Wizard step 4: Select the WAN interface
Next, you will be asked which interface that will be used to connect to an ISP for Internet access.
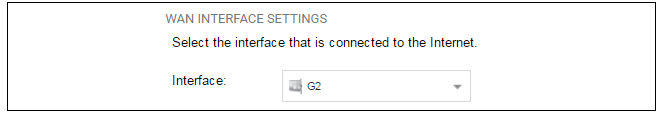
Wizard step 5: Select the WAN interface settings
This step selects how the WAN connection to the Internet will function. It can be one of Manual configuration, DHCP, PPPoE or PPTP as shown below.
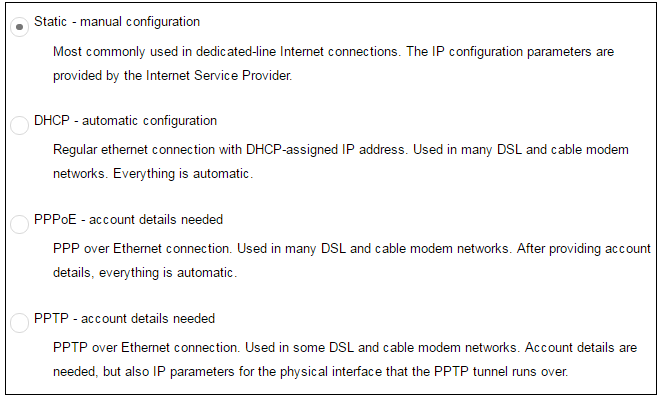
These four different connection options are discussed next in the subsections 5A to 5D that follow.
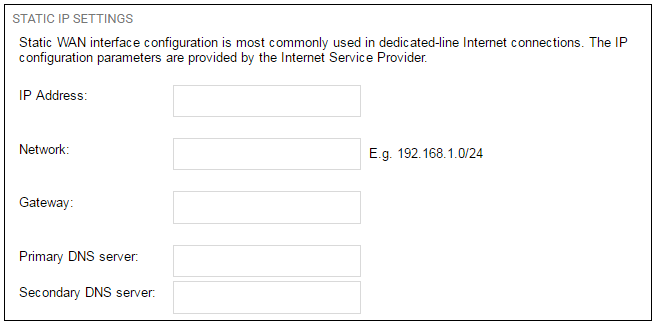
5A. Static - manual configuration
Information supplied by the ISP should be entered in the next wizard screen. All fields need to be entered except for the Secondary DNS server field.
5B. DHCP - automatic configuration
All required IP addresses will automatically be retrieved from the ISP's DHCP server with this option. No further configuration is required for this so it does not have its own wizard screen.
5C. PPPoE settings
The username and password supplied by an ISP for PPPoE connection should be entered. The Service field should be left blank unless the ISP supplies a value for it.
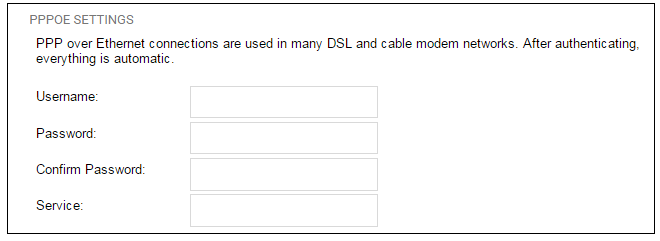
DNS servers are set automatically after connection with PPPoE.
5D. PPTP settings
The username and password supplied by an ISP for PPTP connection should be entered. If DHCP is to be used with the ISP then this should be selected, otherwise Static should be selected followed by entering the static IP address supplied by the ISP.
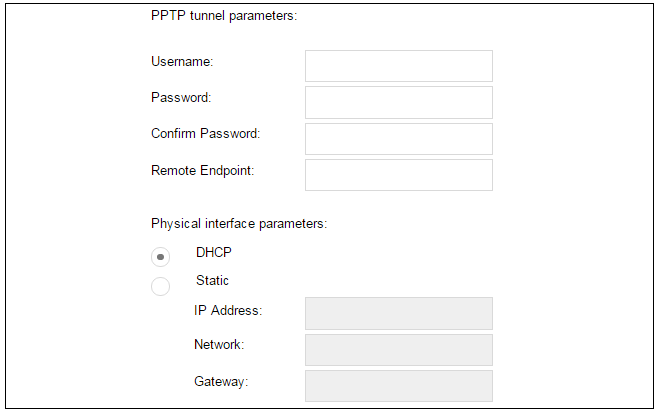
DNS servers are set automatically after connection with PPTP.
Wizard step 6: DHCP server settings
If the firewall is to function as a DHCP server, it can be enabled here in the wizard on a particular interface or configured later.The range of IPv4 addresses that can be handed out must be specified in the form n.n.n.n-n.n.n.n, where n is a number between 0 and 255 and n.n.n.n is a valid IPv4 address within a subnet local to the firewall.
For example, the private IPv4 address range might be specified as 192.168.1.50 - 192.168.1.150 with a netmask of 255.255.255.0.
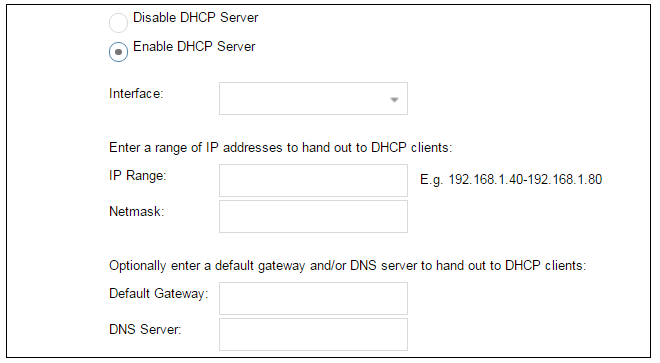
For the default gateway, it is recommended to specify the IPv4 address assigned to the internal network interface. The DNS server specified should be the DNS supplied by an ISP.
Wizard step 7: Helper server settings
Optional NTP and Syslog servers can be enabled here in the wizard or configured later. Network Time Protocol servers keep the system date and time accurate. Syslog servers can be used to receive and store log messages sent by cOS Core. By selecting the Clavister option, the current time will be updated over the Internet from Clavister's own timeserver.
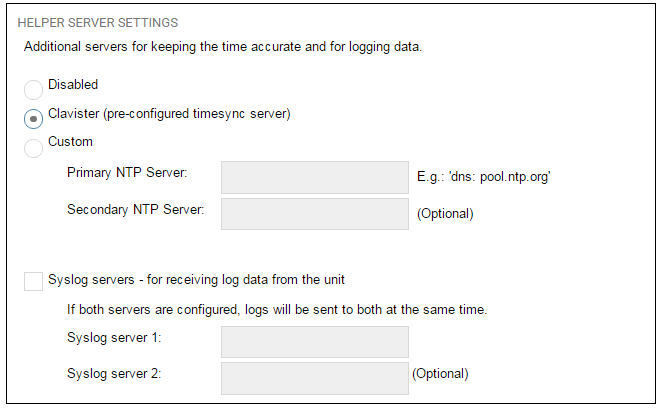
When specifying a hostname as a server instead of an IP address, the hostname should be prefixed with the string dns:. For example, the hostname host1.company.com should be entered as dns:host1.company.com.
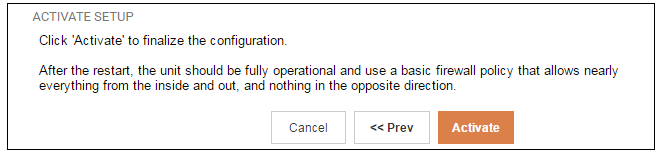
Wizard step 8: Activate setup
The final step for the configuration is to save and activate it by pressing the Activate button. After this step the Web Interface returns to its normal appearance and the administrator can continue to configure the system.
Wizard step 9: License Activation
This last and optional step is to install a license which is fetched automatically from Clavister servers. Internet access must have been set up in previous wizard steps for this option to function. The only input required is the MyClavister username and password for the Clavister website. This also creates a lasting link between the 6000 Series and the Clavister servers so that any future license updates can be installed automatically.
If customer registration has not been previously been done, a link is provided to open a browser window to complete registration. After registration, come back to this step.
Alternatively, this step can be skipped and license installation can be done later, in which case cOS Core will run in demo mode with a 2 hour time limit. After the 2 hour period, only management access will be allowed.
If a license is installed at this point, the wizard will then ask if a reconfigure or restart operation should be performed. To ensure that the 6000 Series can make use of the full capabilities of the license, the restart option should be chosen.
Running the Wizard Again
Once the wizard has been successfully finished and activated, it cannot be run again. The one exception to this is if cOS Core has its default configuration restored as part of a factory reset. In this case, cOS Core will behave as though it were being started for the first time.