| Home Prev |  cOS Core 14.00.15 Administration Guide cOS Core 14.00.15 Administration Guide
|
Next |
|---|
Overview
An IP Policy object provides the option to apply Automatic Address Translation of the source address (this option does not exist in IP rules). This is enabled by setting the Source Translation property of an IP policy to a value of Auto (this is also the default value for the property).The automatic translation option is useful to quickly set up the following scenarios:
Internal clients with private IPv4 addresses require access to the Internet as well as other private addresses. Setting this up is described in Section 8.5.1, NAT Only Translation.
SAT translation is required to a protected local webserver that also must be accessed by internal clients with private IPv4 addresses. Setting this up is described in Section 8.5.2, NAT/SAT Translation.
What Automatic Translation Does
Automatic translation is enabled by using the Auto option for source address translation in an IP Policy object and this is selected by default. If the Action property of the IP policy is Allow, cOS Core will decide which, if any, translation to perform by applying the rules summarized in the table below.| # | Type of Source IP | Type of Destination IP | Action Taken |
|---|---|---|---|
| 1 | Public | Private or Public | Allow with no translation. |
| 2 | Private | Public | NAT using the destination interface's IP. |
| 3 | Private |
Private and Destination Translation = SAT and Source Network contains the SAT IP. |
NAT using the destination interface's IP. |
| 4 | Private |
Private and the previous action didn't trigger. |
Allow with no translation. |
The following is a more detailed description of the actions in the above table:
If the connection's source IP address is a public address:
cOS Core will Allow traffic from the source address to the destination address.
If the connection's source IP address is a private address:
If the destination address is a public IP address, cOS Core will NAT the source address through the IP address of the destination interface.
If the Destination Translation is set to SAT and the Source Network contains the SAT Destination IP address, cOS Core will NAT the private source address through the IP address of the destination interface. (This allows, for example, a protected webserver to be accessed by internal clients.)
Or if the above is not the case and the destination address is a private IP address, cOS Core will Allow the traffic from the private source address to the private destination address.
The following should be noted about IP policies that make use of automatic translation:
The Source Network and the Destination Network can consist of a mixture of private and public IP addresses.
More than one of the actions described above could be applied by a single IP policy to different connections. The different actions are applied depending on the source and destination address of each connection.
Automatic Translation Has No Effect On Denied Traffic
The Source Translation property setting of an IP policy that denies traffic is not relevant since triggering traffic will always be dropped and no translation will ever take place.Therefore, the Source Translation property can be left at the default value of Auto for a denying IP policy. Such a policy can be seen in Example 3.36, “Creating a Drop-All IP Policy”.
Viewing the Details of Automatic Translation
When the Auto option is used with an IP Policy object, a set of IP Rule objects are created in the background to implement the IP policy. These IP rules are not visible in the Web Interface or InControl. However, if a detailed view of the implementation is required, the CLI command rules can be used to list all the IP rules created.The diagram below illustrates a typical scenario where automatic NAT translation might be used.
In the diagram above, the following types of traffic flows need to be allowed:
The internal clients on the IPv4 network B need access to any other private IP address. Automatic translation always allows traffic between private IPv4 addresses without applying any translation.
The internal clients on the network B need access to the Internet so they require NAT translation of their private IPv4 address to the public IPv4 address of the firewall interface connected to the Internet. Automatic translation always applies NAT translation when a private IPv4 address tries to connect to a public IPv4 address.
All the above requirements or combinations of them can be met using a single IP policy with automatic translation enabled. How to configure this is shown in the example below.
Example 8.13. Automatic NAT Translation with an IP Policy
This example shows how the automatic translation option in a single IP policy can be used so that HTTP/HTTPS clients on lan-net with private IP addresses are connected using automatic NAT translation to the Internet via the single public IP address wan_ip. The diagram below illustrates this scenario.
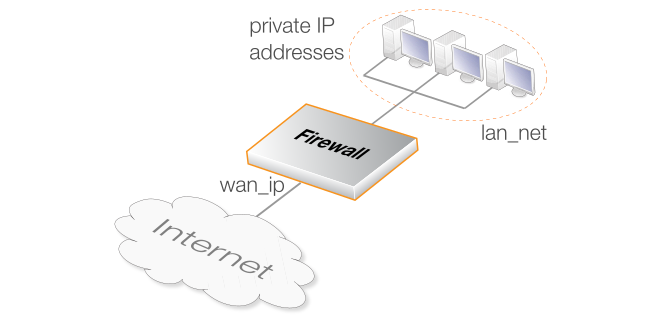
The value for Source Translation defaults to Auto but in these examples it is explicitly stated for clarity.
Command-Line Interface
Create an IP policy with automatic translation:
Device:/> add IPPolicy Name=http_auto_nat_policy
SourceInterface=lan
SourceNetwork=lan_net
DestinationInterface=wan
DestinationNetwork=all-nets
Service=http-all
Action=Allow
SourceAddressTranslation=AutoInControl
Follow similar steps to those used for the Web Interface below.
Web Interface
Create an IP policy with automatic translation:
The diagram below illustrates a typical scenario where automatic NAT/SAT translation might be used. This extends the scenario discussed previously in Section 8.5.1, NAT Only Translation with the additional requirement that connections from the Internet to the firewall's public IP address require SAT translation of the destination address to the private IP address of the webserver.
In the diagram above, the following types of traffic flows need to be allowed:
The internal clients on the IPv4 network B need access to any other private IP address. Automatic translation always allows traffic between private IPv4 addresses without applying any translation.
The internal clients on the network B need access to the Internet so they require NAT translation of their private IPv4 address to the public IPv4 address of the firewall interface connected to the Internet. Automatic translation always applies NAT translation when a private IPv4 address tries to connect to a public IPv4 address.
The webserver in the private IPv4 network A may be accessed by remote clients over the Internet using SAT translation of the firewall's public IP address. Automatic translation can be combined in the same IP policy with one-to-one SAT translation of the destination address to allow this.
Internal clients on the private IPv4 network B also need to access the webserver via its public IP address. The NAT capability of automatic translation, which is mentioned in the second point above, will allow this.
All the above requirements or combinations of them can be met using a single IP policy with automatic translation enabled. How to configure this is shown in the example below.
Example 8.14. Automatic SAT/NAT Translation with an IP Policy
This example shows how a single IP policy with automatic translation enabled can be used so that HTTP/HTTPS clients on both the Internet and lan-net can access a protected web server in the DMZ which has the private IPv4 address 10.0.0.5. Connections to the server will be made via the wan interface which has been assigned the public IP address wan_ip. SAT translation therefore needs to be applied so the destination IP address of connections to the server.
In addition, the clients on lan-net need access to the Internet via the wan interface.
The diagram below illustrates this scenario.
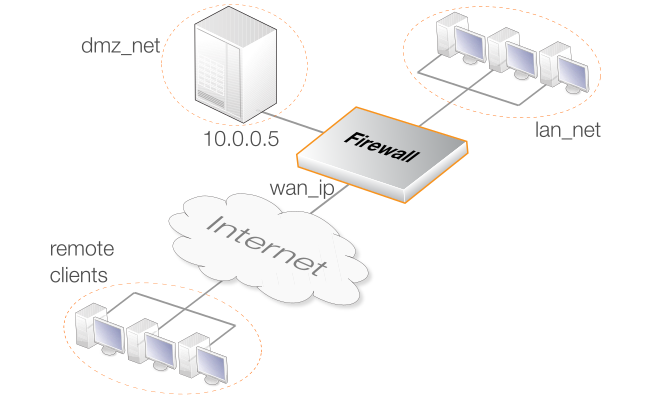
Note that interface value of any and the address book value of all-nets are used in this example for simplicity but these could be narrowed for better security by creating the appropriate Interface Group and IP4 Address objects.
Command-Line Interface
Device:/> add IPPolicy Name=http_auto_satnat_policy
SourceInterface=any
SourceNetwork=all-nets
DestinationInterface=any
DestinationNetwork=wan_ip
Service=http-all
Action=Allow
SourceAddressTranslation=Auto
DestinationAddressTranslation=SAT
DestinationAddressAction=SingleIP
DestNewIP=10.0.0.5InControl
Follow similar steps to those used for the Web Interface below.
Web Interface
![[Note]](images/note.png) |
Clients and server can be on the same network |
|---|---|
|
It should be noted that the above example would allow not allow not only clients on the DMZ to access the webserver via its public IP address but also clients that are the same network as the webserver. |