| Home Prev |  InControl 4.01.01 Administration Guide InControl 4.01.01 Administration Guide
|
Next |
|---|
A more sophisticated logging facility than Memlog is provided by the proprietary Clavister InControl Logging Agent (ILA). This software component comes with the InControl installation package and functions as an optional separate, independent server for receiving and storing cOS Core log event messages.
The ILA can capture the raw log messages generated by any number of firewalls that are managed by InControl. The ILA log event database can then be analyzed through report generating features integrated into the InControl client. The log messages are sent to the ILA in a proprietary binary file format with the filetype .fwl and these will be referred to as "raw log messages" in this document.
The diagram below shows how ILA fits into InControl usage. Several firewalls can send messages to the ILA and InControl clients manage it, as well as send log queries to it, via the InControl server. All communication between clients and the ILA are mediated by the InControl server. The ILA and the InControl server could be installed on separate computers or the same computer and could be on the same or separate networks.
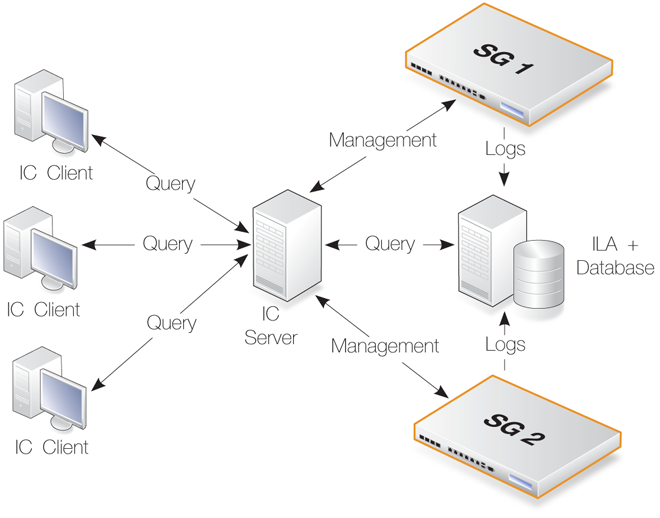
Creating Multiple ILA Instances
To separate the log messages coming from different firewalls or groups of firewalls, it is also possible to create multiple ILA instances with separate log messages databases. This can be particularly useful in a cloud computing environment. Doing this is discussed in Section 23.3, Running Multiple ILAs. However, reading this section first is recommended to understand basic ILA installation and operation.ILA Installation
ILA installation can be performed as part of running the InControl installer and can be installed together with the server and client on the same computer. However, the installer also allows ILA to be installed separately on a different computer. components.The ILA is always installed on the same computer as the files which store received raw log messages. If installed on a separate computer, the ILA must have a network connection to its associated InControl server. This connection can be local or could be made remotely over the public Internet.
More than one ILA installation can be fed by messages from a single firewall. Similarly, one ILA installation can receive log messages from multiple firewalls. This is determined by what log servers cOS Core is configured to send messages to.
ILA Network Communication Uses Port 5555
If the InControl server and the ILA are running on the same computer, there will be no problem with port usage and communication between them.However, if the ILA runs on a separate computer then that computer must allow incoming TCP and UDP connections on port 5555. TCP port 5555 is used when adding an ILA and/or deploying ILA configurations. UDP port 5555 is used when the InControl server polls the ILA for online status.
The ILA runs as two separate windows services which are constantly running. These two services are:LogReceiver.exe
This process performs the logging function of the ILA. It receives log messages and stores them in ILA's raw log database.
The Status column of the Logging Agent tab in the InControl client does not indicate the status of this process.
ILA.exe
If the Log Analyzer feature is enabled, this process builds the log analyzer database. This analyzer database is separate from the log receiver's raw log database.
The process also performs all query functions. That is to say, all queries launched from either the Log Explorer or Log Analyzer features in the InControl client.
If a query is launched and this service is not running, the client will return an error message.
The Status column of the Logging Agent tab in the InControl client does indicate the status of this process.
![[Important]](images/important.png) |
Important: ILA services must run under same Windows account |
|---|---|
|
By default, the services LogReceiver.exe and ILA.exe will run under the same Windows user account. This should not be changed. If they run under two different accounts, the ILA will not function. |
The reason for having two services for the ILA is to allow the LogReceiver.exe service to be as efficient and robust as possible. If any execution bottlenecks occur in the ILA.exe service, they will not affect log message processing.
If either of the ILA processes stops running for some reason, Windows will wait one minute before it automatically tries to restart the service.
Unlike the InControl server, the ILA does not have its own graphical user interface to stop or start its Windows services. If the ILA services might not be running then the status should be checked. One symptom is this if the logging agent has a status of offline in the client. Another symptom is if log queries are failing to execute.To check the ILA services in Windows, open the Windows services management tool. Look for Logging Agent and Log Receiver in the list.
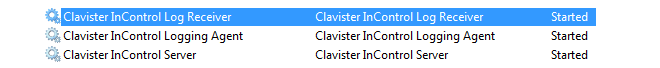
The status for both should be Started if the services are running normally. If the status for either is Stopped then they can be restarted by right clicking the service line and selecting the menu option Action > Start.
Using a Local User Account
Like the installation of the InControl server, if running on a separate computer, it is recommended to use the same, separate, local user account for the ILA installation and running ILA. A local account cannot be logged into remotely, thereby increasing security.![[Important]](images/important.png) |
Important: The ILA service needs administrator privileges |
|---|---|
|
After ILA installation, the Windows service ILA.exe should be run under the local user account and this account should have administrator privileges over the ILA raw log database folder. Administrator privileges allow the ILA server to create new raw log message files. |
Installing Over Older Versions
When installing over an older version of the ILA, there is no requirement for uninstalling the old version first. In addition, the ILA servers does not require that its Windows service is halted first. This occurs automatically.ILA Server and InControl Server Communication
Communication between the InControl server and the ILA is achieved using the Clavister proprietary, secure Netcon protocol. Netcon requires that an agreed Secret Key is used by both sides of the communication.By default, the ILA and server use an agreed, predefined secret key. This is displayed in the ILA configuration dialog available through the InControl client and which is discussed later in this section.
If the ILA server is running on the same PC as InControl, the IP address for access is 127.0.0.1.
Configuring cOS Core for ILA Logging
For each firewall, cOS Core should be configured to specify which loggers to send messages to and which messages to send. The term Logging Agent is used to refer to an ILA server.To specify a new ILA server, first press the Logging Agents button in the ribbon toolbar of the Home tab.
This will open the Logging Agents tab. To define a new ILA server, press the Add button and a new Logging Agent dialog will open.
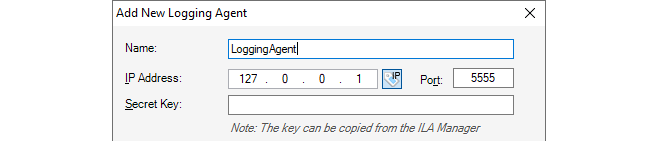
In the example shown above, a symbolic name of My_ILA_server is given for the server. The IP address is given a default value of 127.0.0.1 (the loopback IP address) which will be correct if the ILA server is on the same computer as the InControl server.
The secret key is unique for each ILA instance and must be filled in manually. The key can be found and copied into the system clipboard by opening the separate Logging Agents Manager application and opening the properties for the ILA instance. The first ILA instance is always called "Default". Using the Logging Agents Manager software is described further in Section 23.3, Running Multiple ILAs and it is installed automatically along with other InControl components.
After clicking OK, this server definition will now appear in the Logging Agents tab.
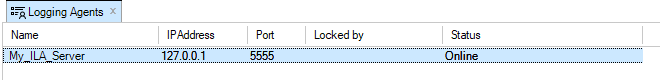
The Online field indicates that connection to this ILA server by the InControl server was successful. The Locked by field indicates any client that is currently editing the properties of this server.
Editing the ILA Server Configuration
The Logging Agents tab also provides the ability to configure the ILA server since, unlike the InControl server, there is no separate graphical interface for doing this.
This brings up the ILA configuration dialog.
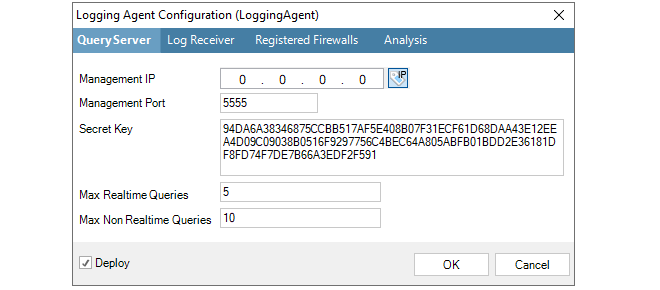
Here, the Management IP is the source IP address for management connections to the ILA server. The management IP address of the ILA server itself is specified in the ILA Properties dialog.
To configure the ILA to accept and store log messages coming from a particular firewall, select the Registered Firewalls tab and press the plus "+" button.
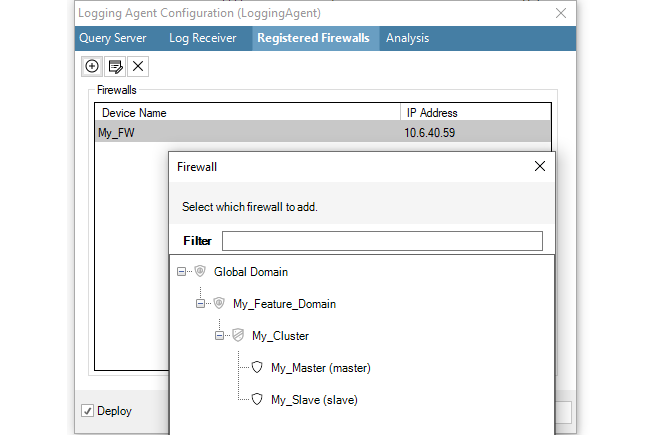
After selection, the chosen firewall will appear in the Registered Firewall list and the IP Address value for the firewall will default to the management IP address of the firewall and this is the address from which the ILA will expect log messages.
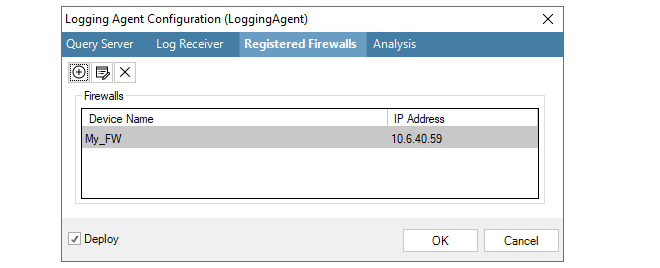
If necessary, this address can be changed by selecting the firewall line, pressing the edit button in the dialog and entering a new value, as shown in the example below where the firewall called My_FW will send log messages from the IP address 10.6.40.52.
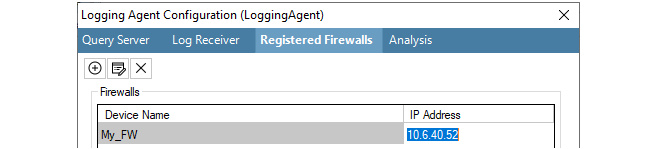
The ILA configuration dialog has the option to deploy immediately after the dialog closes Alternatively, the deployment can be done using the separate deploy button in this tab's toolbar. Deployment means that the new settings are sent via the InControl server to the ILA server.
If the ILA server configuration has been changed but not deployed, an alarm will be created in the alarm list to indicate this.
Finally, the firewall itself must be configured to send log messages directly to the ILA server. This is done by selecting System then Log and Event Receivers and adding an FWLog Receiver.
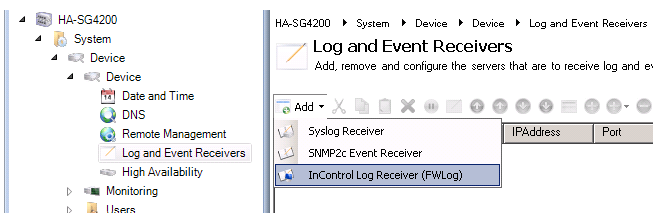
The log receiver should be configured with the IP address and port number that is configured for the ILA server. Below, the defaults are specified.
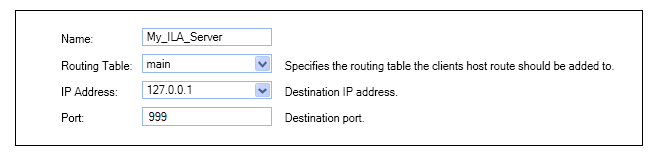
Changing the Secret Key
Changing the secret key of the ILA server is a two-step process where the key has to be changed first on the ILA server and then the local client:Press the Configure button, change the secret key in the ILA server configuration and deploy the new configuration to the server.
Right-click the ILA server in the server list and select Properties to display the properties dialog. Now, set the secret key to the same value that was deployed to the server in the previous step and close the dialog.
Troubleshooting ILA Setup Problems
Troubleshooting problems with ILA setup and successful operation is discussed further in a Clavister Knowledge Base article which can be found at the following link:https://kb.clavister.com/324735475
ILA Raw Log Database Management
The ILA raw log database management options are found in ILA configuration dialog. Access this by selecting the ILA server in the Logging Agents tab and pressing the Properties button in the tab's toolbar.
Now select the Log Receiver tab in the dialog.
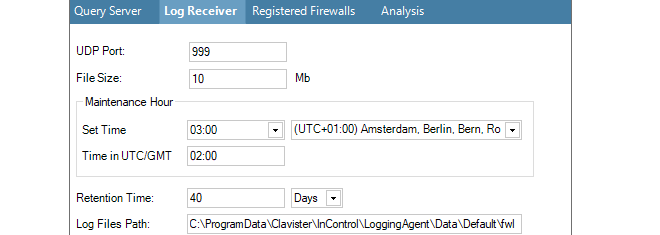
The following parameters are relevant to the raw log database:
File Size (Mb)
This value specifies the maximum file size of the individual files that store log data. The maximum size for this setting is limited to 200 MBytes. It is not related to the total size of the raw log database since the database consists of many of these files. However, the maximum size can affect search speeds.
The raw log database structure consists of a folder for each firewall that is generating logs. Within each firewall folder there is a folder for all the raw log files for each month. At the start of a new day, a new daily log file is created in the relevant month folder. When this daily file reaches the configured maximum size it is closed, compressed using the GZIP algorithm and an additional raw log file is started for that day.
The advantage of this scheme is in searching logs. Each storage file begins with the start and end time of the logs it contains. This means that logs for a particular time interval can be found quickly provided the individual log files are not too large.
Maintenance Hour
This parameter specifies the time of day when routine maintenance will take place. In the example shown above, 3.00 in the morning has been specified.
Retention Time
When the routine maintenance process runs, it deletes any files that are older than this numbers of days. This setting is the principle means of controlling the disk space occupied by the ILA raw log database.
![[Note]](images/note.png) |
Note: Setting the ILA retention time value |
|---|---|
|
It is up to the administrator to determine an appropriate value for the retention time setting. It should be based on the amount of free disk space available and the expected rate of increase in the raw log files. A useful exercise for making this determination is to observe the size expansion over a few days of typical system usage. If an ILA instance is running on the same computer as the InControl server, the ILA raw log database size will contribute to the alert that the InControl server generates should free disk space fall below the configured value. |
Log Files Path
This is the file system location used to initially store the incoming raw log messages being sent by monitored firewalls. The log messages sent by cOS Core are in a special .fwl binary format and should not be read outside of InControl. To examine the received messages, the InControl Log Explorer tab must be opened, an ILA instance selected from the list and the Open > Log Files option selected.
Raw Log Folders and File Naming
As discussed above, ILA keeps raw log messages in files that have a configured maximum size. These files are organized in the following way:For each month of operation, a folder is created with a folder name made up of the current year and month. For example, the folder name used for the log files created during August 2011 is "201108".
The messages received for each new day within a month are placed in that month's folder and each log file created is given a name of the form:
<day>-<suffix>
For example, the first log file created on the first of any month has the name "1-0.fwl". The first file created for the second day of any month is "2-0.fwl".
When files reach the configured size limit and a new log file is created for that day, the filename is the same except for the suffix which becomes "-1", "-2" and so on for subsequent files. For example, when the first file for the first of the month reaches the configured limit, the second file created for that day is given the name "1-1.fwl". At the same time, the previous file is compressed using GZIP and its name is changed to "1-0.gz".
All raw log files for a particular firewall are stored in a folder dedicated to that firewall and these are stored within the ILA main database folder. Each firewall folder name is created from the unique firewall ID number (since the firewall name can change). The configuration file ILA.xml contains a mapping of a firewall's ID number to its IP address.
Optimizing InControl Log File Storage
The administrator has various options to best optimize InControl log file storage. These are discussed in a Clavister Knowledge Base article which can be found at the following link:https://kb.clavister.com/324735449
ILA Logging Without InControl Management
Sometimes there may be a requirement to have a firewall send log messages to an ILA server but not give InControl management rights over the firewall.When InControl can manage a firewall it means its Netcon Keys have been added to InControl and any InControl client then has the potential to read and change the configuration. If the aim is just to enable ILA logging, then this can be done without giving the keys to InControl using the following steps:
Open the InControl client and select the Firewalls tab.
Add the firewall and give it a name but mark the firewall as being Offline. This means that InControl will not try to contact the firewall.
In the Logging Agents tab, bring up the Configuration dialog of the target ILA server, select the Registered Firewalls tab and add the newly defined firewall.
If the Log Analyzer function is also to be used, the firewall should be added under the Analysis tab (this can be done later).
When the dialog's OK button is pressed, this ILA configuration is deployed to the ILA server.
Stop both ILA Windows services. This is done in Windows by starting the utility services.msc in a command console. Locate the LogReceiver and ILA service then stop them. Leave the utility open to restart the service later.
The ILA configuration file ila.xml now needs to be manually altered. This file is located in the following folder depending on the version history of InControl:
For an InControl installation that has been upgraded to InControl version 1.83 or later, the file is located within the path %appdata%\Clavister\InControl\LoggingAgent\Config. Where %appdata% represents the user account that performed the initial installation of InControl.
For a new installation of InControl from version 1.83 or later, the file can be found within the path %programdata%\Clavister\InControl\LoggingAgent\Config.
Under the above path's Config folder is a separate configuration files folder for each logging agent instance that has been created and with the name of that instance. If no extra instances have been created then only the default folder called Default will exist within the Config folder.
After opening the relevant ila.xml file in a text editor, change the firewall's IP from the default of 0.0.0.0 to the actual IP address of the firewall. Save this change.
Every time the a new ILA configuration is deployed, this setting will be reinitialized to 0.0.0.0 and this step must therefore be repeated.
Now restart LogReceiver and ILA services then close the services.msc utility.
In a later version of InControl these steps will not be required and it will be possible to enable this option through a simple checkbox selection.