| Home Prev |  InControl 4.01.01 Administration Guide InControl 4.01.01 Administration Guide
|
Next |
|---|
It is possible to set up shared IP policies so that an IP rule set defined within an InControl domain can be shared across multiple cOS Core firewalls within that domain. This means that any changes made to the shared rule set will be automatically reflected in all the firewalls that share it. This feature is also sometimes referred to as Shared IP Rule Sets.
A Summary of Setup Steps
The following steps provide a simplified summary of how to set up a shared IP rule set:Define any required Zone objects in the InControl global domain or a subdomain. Shared IP rule set entries can only refer to interfaces using zones so these new zones will represent Ethernet interfaces with similar functions on different firewalls. These zones will also have to be assigned to the relevant Ethernet interfaces in each individual firewall configuration using InControl.
Note that zone names should be made unique across domains and should not duplicate any zone names in the firewalls that will share rule sets.
Create a new IP rule set under the Policies > Firewalling > Rules > Additional IP Rule Sets folder in the global domain (or subdomain) and add any shared entries, such as IP policies, to this new rule set. If an entry specifies a specific Ethernet interface, one of the zone names created above must be selected.
In the configuration of each firewall that will share the rule set, insert a Goto rule at the appropriate point in each firewall's IP rule set. This may be in the predefined main IP rule set but it could be in another, administrator defined, IP rule set.
The Goto rule must reference the shared rule set in the global domain (or subdomain containing the firewall) by name.
A detailed example that shows how these steps are applied is given at the end of this chapter.
Specifying Interface Names in Shared IP Rule Sets
The entries in a shared rule might have traffic filtering parameters set and these can trigger on the usual combinations of source/destination, interface/IP and service. However, since shared rule sets might be used by different types of cOS Core platforms with different local Ethernet interface names, interfaces in shared rules sets can only take one of the following values:
core - cOS Core itself. This might be used when allowing ICMP traffic.
any - Any interface on the firewall.
A zone name - An administrator defined zone defined within the domain.
If a zone name is to be used, that zone must already be defined in the global domain or the subdomain and it must also be assigned to the relevant interface in the firewall configuration that will use the shared IP rule set. In summary, a zone is simply a logical name that can be assigned to any cOS Core interface so that it is possible to have a common designation for Ethernet interfaces with similar usage on dissimilar computing platforms.
For example, all the Ethernet interfaces on a set of dissimilar firewalls that are connected to the Internet might be assigned the zone called wan_zone. Using zones in cOS Core is described further in the Zones section of the separate cOS Core Administration Guide.
The effect of the Goto rule in a firewall's IP rule set is to direct rule set processing to the shared rule set when it is encountered. In addition, a Return rule could be used at the end of the shared rule set to direct processing back to the position after the Goto. More explanation about the use of these directives in rule set processing can be found in the Multiple IP Rule Sets section of the separate cOS Core Administration Guide.When shared IP rules sets are set up in this way, InControl keeps a master copy of the rule set in the global domain or a subdomain but it also loads a copy of the rule set into each firewall that shares it. This means that there is no need to go back to the InControl server to scan the shared rule set and so there is no performance penalty when using shared rule sets.
It also means that these shared rule sets are visible in the firewall configuration if they are examined locally, outside of InControl, and they will remain present if the firewall is removed from InControl management.
Notes About Usage
The following should be noted when using shared IP rule sets:Multiple shared IP rule sets can be created in the same domain for different purposes.
Shared IP rule sets can contain any type of entry that can be found in a firewall IP rule set. However, specific Ethernet interfaces can only be selected using their assigned zone. The zones referenced must exist in the same domain or an enclosing domain (such as the global domain).
A Goto entry referencing the shared rule set might be inserted into the firewall's predefined main IP rule set, but it does not have to be. Another, administrator created IP rule set, could point to a shared rule set.
Since the Goto reference is by name, the name of a shared IP rule set must be unique within the available shared rule sets. There must also not be another local IP rule set in the firewall's configuration with that name.
Shared rule sets defined in a subdomain will only be available to the firewalls within that subdomain. Shared rule sets in the global domain are available to all firewalls.
If there is no Return entry in a shared IP rule set, rule scanning will stop at the last entry in that rule set.
A shared IP rule set could contain a Goto which references another shared rule set.
An Example of Setting Up Shared IP Policies
The following steps provide a detailed example of setting up share IP policies. Setting up zones and assigning them to firewall interfaces is not included.Create a new IP rule set Policies > Firewalling > Rules > Additional IP Rule Sets folder in the global domain. In this case, the new rule set will be called MyAdditional_IP_Ruleset.
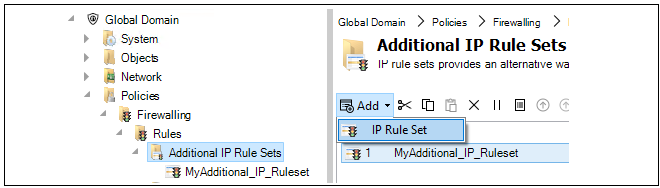
Add any rule set entries to the additional IP rule set that are to be shared between firewalls.
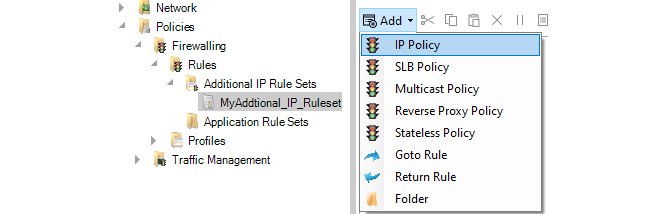
For each firewall that will share this new rule set, open the relevant IP rules set in the local firewall configuration and add a Goto rule that directs rule processing to the shared rule set.
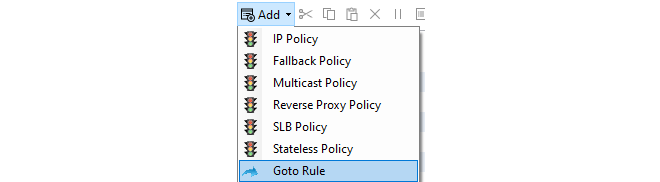
When the Goto rule is defined, specify the name of the shared rule set as the target. In the example below, the Goto rule called GotoAdditionalIPRuleset points to the share rule set defined earlier called MyAdditional_IP_Ruleset. Optionally, the Goto rule could be created to only trigger on a given combination of source/destination, interface/IP and source.
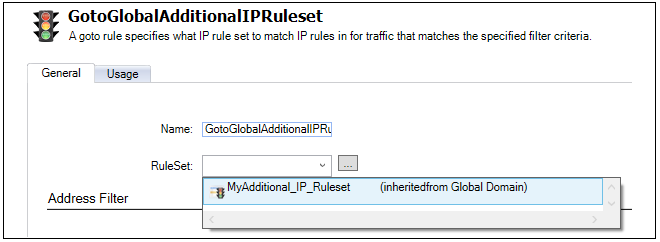
Check in all the changes. The modified firewall will now use the shared IP rule set if the Goto entry is encounted during IP rule set processing.