| Home Prev |  cOS Core 14.00.15 Administration Guide cOS Core 14.00.15 Administration Guide
|
Next |
|---|
The Multicast Problem
Certain types of Internet interactions, such as conferencing and video broadcasts, require a single client or host to send the same packet to multiple receivers. This could be achieved through the sender duplicating the packet with different receiving IP addresses or by a broadcast of the packet across the Internet. These solutions waste large amounts of sender resources or network bandwidth and are therefore not satisfactory. An appropriate solution should also be able to scale to large numbers of receivers.The Multicast Routing Solution
Multicast Routing solves the problem by the network routers themselves, replicating and forwarding packets via the optimum route to all members of a group.The IETF standards that allow multicast routing are the following:
Class D of the IPv4 address space which is reserved for multicast traffic. Each multicast IP address represents an arbitrary group of recipients.
The Internet Group Membership Protocol (IGMP) allows a receiver to tell the network that it is a member of a particular multicast group.
Protocol Independent Multicast (PIM) is a group of routing protocols for deciding the optimal path for multicast packets.
Underlying Principles
Multicast routing functions on the principle that an interested receiver joins a group for a multicast by using the IGMP protocol. PIM routers can then duplicate and forward packets to all members of such a multicast group, thus creating a distribution tree for packet flow. Rather than acquiring new network information, PIM uses the routing information from existing protocols, such as OSPF, to decide the optimal path. A key mechanism in the multicast routing process is Reverse Path Forwarding. For unicast traffic, a router is concerned only with a packet's destination. With multicast, the router is also concerned with a packets source since it forwards the packet on paths which are known to be downstream, away from the packet's source. This approach is adopted to avoid loops in the distribution tree.Routing to the Correct Interface
By default, multicast packets are routed by cOS Core to the core interface (in other words, to cOS Core itself). Multicast Policy objects are created in the IP rule set in order to perform forwarding to the correct interfaces. This is demonstrated in the Example 4.16, “Multicast Forwarding With No Address Translation”. If an IP rule set entry exists which applies to a multicast packet's destination IP address, then that Ethernet interface automatically gets its receive mode set to promiscuous in order to receive multicast packets. Promiscuous mode means that traffic with a destination MAC address that does not match the Ethernet interface's MAC address will be sent to cOS Core and not discarded by the interface. Promiscuous mode is enabled automatically by cOS Core and the administrator does not need to worry about doing this.With multicast only, the usage of promiscuous mode can be explicitly controlled using the Ethernet object property Receive Multicast Traffic which has a default value of Auto. If this property is set to Off, the multicast forwarding feature cannot function.
If the administrator enters a CLI ifstat <ifname> command, the Receive Mode status line will show the value Promiscuous next to it instead of Normal to indicate the mode has changed. This is discussed further in Section 3.4.2, Ethernet Interfaces.
The Multicast Policy is used to achieve duplication and forwarding of packets through more than one interface. This feature implements multicast forwarding in cOS Core, where a multicast packet is sent through several interfaces.
Note that since this rule overrides the normal routing tables, packets that should be duplicated by the Multicast Policy need to be routed to the core interface.
By default, the multicast IP range 224.0.0.0/4 is always routed to core and does not have to be manually added to the routing tables. Each specified output interface can individually be configured with static address translation of the destination address. The Interface field in the Interface/Net Tuple dialog may be left empty if the IPAddress field is set. In this case, the output interface will be determined by a route lookup on the specified IP address.
The Multicast Policy can operate in one of two modes:
Using IGMP
The traffic flow specified by the Multicast Policy must have been requested by hosts using IGMP before any multicast packets are forwarded through the specified interfaces. This is the default behavior of cOS Core.
Not using IGMP
The traffic flow will be forwarded according to the specified interfaces directly without any interference from IGMP.
Example 4.16. Multicast Forwarding With No Address Translation
This example shows how to configure multicast forwarding together with IGMP. The multicast sender is 192.168.10.1 and generates the multicast streams 239.192.10.0/24:1234. These multicast streams should be forwarded from interface wan through the interfaces if1, if2 and if3. The streams should only be forwarded if some host has requested the streams using the IGMP protocol.
A Multicast Policy object will be created to forward the multicast groups. All groups have the same sender that has the IP address 192.168.10.1, which is located behind the wan interface.
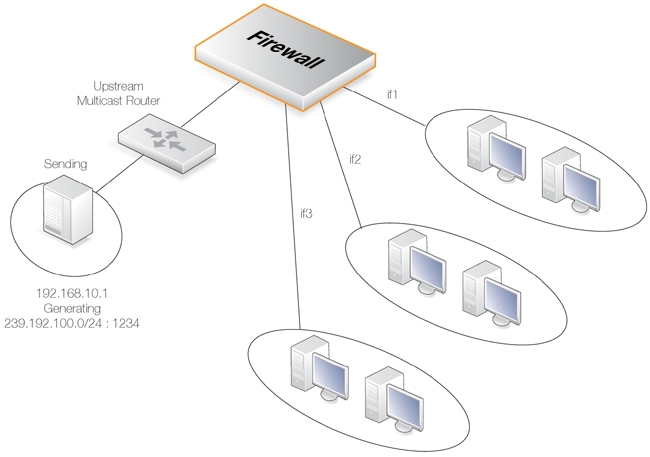
The multicast groups should only be forwarded to the outgoing interfaces if clients behind those interfaces have requested the groups using IGMP. The following steps will configure forwarding of the multicast traffic.
IGMP is configured separately and this is described in Section 4.8.3.2, IGMP Rules Configuration with Address Translation. It is configured in the same way that it is configured when using other IP rule set entries.
InControl
Follow similar steps to those used for the Web Interface below.
Web Interface
A. Create a custom Service object for multicast:
B. Create a Multicast Policy object:
IGMP configuration for this example is described in Section 4.8.3.1, IGMP Rules Configuration with No Address Translation.
Creating a Multicast Policy with the CLI
Creating multicast policies through the CLI requires some additional explanation.The CLI command to create a Multicast Policy is the following:
Device:/> add MulticastPolicy Name=mc_policy1
SourceNetwork=<srcnet>
SourceInterface=<srcif>
DestinationInterface=<srcif>
DestinationNetwork=<destnet>
Service=<service>
MultiplexArgument={outif1;ip1},{outif2;ip2},{outif3;ip3}...The two values {outif;ip} represent a combination of output interface and, if address translation of a group is needed, an IP address.
If, for example, multiplexing of the multicast group 239.192.100.50 is required to the output interfaces if2 and if3, then the command to create the rule would be:
Device:/> add MulticastPolicy Name=mc_policy2
SourceNetwork=<srcnet>
SourceInterface=<if1>
DestinationInterface=core
DestinationNetwork=239.192.100.50
Service=<service>
MultiplexArgument={if2;},{if3;}The destination interface is core since 239.192.100.50 is a multicast group. No address translation of 239.192.100.50 was added but if it is required for, say, if2 then the final argument would be:
MultiplexArgument={if2;<new_ip_address>},{if3;}
Example 4.17. Multicast Forwarding With Address Translation
This example is based on the previous one but this time the multicast group is translated. When the multicast streams 239.192.10.0/24 are forwarded through the if2 interface, the multicast groups should be translated into 237.192.10.0/24. No address translation should be made when forwarding through interface if1. This is illustrated in the diagram below.
InControl
Follow similar steps to those used for the Web Interface below.
Web Interface
A. Create a custom service for multicast called multicast_service:
B. Create a Multicast Policy:
IGMP configuration for this example is described in Section 4.8.3.2, IGMP Rules Configuration with Address Translation.
IGMP signaling between hosts and routers can be divided into two categories:
IGMP Reports
Reports are sent from hosts towards the router when a host wants to subscribe to new multicast groups or change current multicast subscriptions.
IGMP Queries
Queries are IGMP messages sent from the router towards the hosts in order to make sure that it will not close any stream that some host still wants to receive.
Normally, both types of rule have to be specified for IGMP to function but there are two exceptions:
If the multicast source is located on a network directly connected to the router, no query rule is needed.
If a neighboring router is statically configured to deliver a multicast stream to the Clavister firewall, an IGMP query would also not have to be specified.
cOS Core supports two IGMP modes of operation:
Snoop Mode
Proxy Mode
The operation of these two modes are shown in the following illustrations:
In Snoop Mode, the Clavister firewall will act transparently between the hosts and another IGMP router. It will not send any IGMP Queries. It will only forward queries and reports between the other router and the hosts.
In Proxy Mode, the firewall will act as an IGMP router towards the clients and actively send queries. Towards the upstream router, the firewall will be acting as a normal host, subscribing to multicast groups on behalf of its clients.
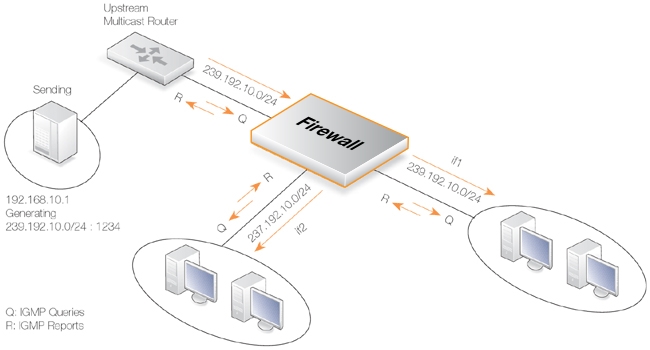
This example describes the IGMP rules needed for configuring IGMP rules for Example 4.16, “Multicast Forwarding With No Address Translation”. No Address Translation scenario described above. The router is required to act as a host towards the upstream router and therefore IGMP must be configured to run in proxy mode.
Example 4.18. IGMP - No Address Translation
The following example requires a configured interface group IfGrpClients including interfaces if1, if2 and if3. The IP address of the upstream IGMP router is known as UpstreamRouterIP.
Two rules are needed. The first one is a report rule that allows the clients behind interfaces if1, if2 and if3 to subscribe for the multicast groups 239.192.10.0/24. The second rule, is a query rule that allows the upstream router to query us for the multicast groups that the clients have requested.
The following steps need to be executed to create the two rules.
InControl
Follow similar steps to those used for the Web Interface below.
Web Interface
A. Create the first IGMP Rule:
B. Create the second IGMP Rule:
The following examples illustrates the IGMP rules needed to configure IGMP according to the Address Translation scenario described above in Example 4.17, “Multicast Forwarding With Address Translation”. We need two IGMP report rules, one for each client interface. The interface if1 uses no address translation and if2 translates the multicast group to 237.192.10.0/24. We also need two query rules, one for the translated address and interface, and one for the original address towards if1.
Two examples are provided, one for each pair of report and query rules. It is assumed the upstream multicast router uses the IP address UpstreamRouterIP.
Example 4.19. Interface if1 Configuration
The following steps needs to be executed to create the report and query rule pair for if1 which uses no address translation.
InControl
Follow similar steps to those used for the Web Interface below.
Web Interface
A. Create the first IGMP Rule:
B. Create the second IGMP Rule:
Example 4.20. Interface if2 Configuration - Group Translation
The following steps needs to be executed to create the report and query rule pair for if2 which translates the multicast group. Note that the group translated therefore the IGMP reports include the translated IP addresses and the queries will contain the original IP addresses
InControl
Follow similar steps to those used for the Web Interface below.
Web Interface
A. Create the first IGMP Rule:
B. Create the second IGMP Rule:
![[Tip]](images/tip.png) |
Advanced IGMP Settings |
|---|---|
|
There are a number of IGMP advanced settings which are global and apply to all interfaces which do not have IGMP settings explicitly specified for them. |
The following advanced settings for IGMP can be found in the Web Interface by going to:
Network > Routing > Advanced Multicast Settings
Auto Add Multicast Core Route
This setting will automatically add core routes in all routing tables for the multicast IP address range 224.0.0.0/4. If the setting is disabled, multicast packets might be forwarded according to the default route.Default: Enabled
IGMP Before Rules
For IGMP traffic, by-pass the normal IP rule set and consult the IGMP rule set.Default: Enabled
IGMP React To Own Queries
The firewall should always respond with IGMP Membership Reports, even to queries originating from itself. Global setting on interfaces without an overriding IGMP Setting.Default: Disabled
IGMP Lowest Compatible Version
IGMP messages with a version lower than this will be logged and ignored. Global setting on interfaces without an overriding IGMP Setting.Default: IGMPv1
IGMP Router Version
The IGMP protocol version that will be globally used on interfaces without a configured IGMP Setting. Multiple querying IGMP routers on the same network must use the same IGMP version. Global setting on interfaces without an overriding IGMP Setting.Default: IGMPv3
IGMP Last Member Query Interval
The maximum time in milliseconds until a host has to send an answer to a group or group-and-source specific query. Global setting on interfaces without an overriding IGMP Setting.Default: 5,000
IGMP Max Total Requests
The maximum global number of IGMP messages to process each second.Default: 1000
IGMP Max Interface Requests
The maximum number of requests per interface and second. Global setting on interfaces without an overriding IGMP Setting.Default: 100
IGMP Query Interval
The interval in milliseconds between General Queries sent by the device to refresh its IGMP state. Global setting on interfaces without an overriding IGMP Setting.Default: 125,000
IGMP Query Response Interval
The maximum time in milliseconds until a host has to send a reply to a query. Global setting on interfaces without an overriding IGMP Setting.Default: 10,000
IGMP Robustness Variable
IGMP is robust to (IGMP Robustness Variable - 1) packet losses. Global setting on interfaces without an overriding IGMP Setting.Default: 2
IGMP Startup Query Count
The firewall will send IGMP Startup Query Count general queries with an interval of IGMPStartupQueryInterval at startup. Global setting on interfaces without an overriding IGMP Setting.Default: 2
IGMP Startup Query Interval
The interval of General Queries in milliseconds used during the startup phase. Global setting on interfaces without an overriding IGMP Setting.Default: 30,000
IGMP Unsolicited Report Interval
The time in milliseconds between repetitions of an initial membership report. Global setting on interfaces without an overriding IGMP Setting.Default: 1,000
It is possible to tunnel cOS Core multicast between two Clavister firewalls through a GRE tunnel. The multicast server will be behind one firewall and the clients behind the other with a GRE tunnel linking the two firewalls.
Setup Issues
There are certain issues that must be noted with tunneling multicast:Make sure that the multicast server is sending the stream with a higher TTL than 1 (VLC uses TTL=1 by default).
When using IGMP, make sure that the destination network is not set to all-nets. If it is, the multiplex rule will not forward the stream to the correct interface.
Multicast Policy rule set entries must be set up both on the firewall that the server is behind and on the firewall that the clients are behind (in other words, the tunnel terminator).
Incoming and outgoing IGMP rules for reporting and querying must be configured on both sides of the tunnel if IGMP is used.
Tunneling Setup Summary
The following components are needed on both the client and server side:Configure a GRE Tunnel object with the remote network being the client network for the server side and the server network on the client side.
Configure routes that route multicast traffic bound for the network on the other side through the GRE tunnel.
Configure a Multicast Policy on both sides.
For the Multicast Policy objects, enable the option: Multicast traffic must have been requested using IGMP before it is forwarded.
Configure IGMP rule objects for the multicast traffic.
An Example Configuration
An example multicast tunneling scenario is illustrated below.The IPv4 address book object called mc_group on both sides of the tunnel is the same multicast IPv4 range. In this example, 239.100.100.0/24.
A. Server Side Configuration Setup
For the server side configuration, assume the client network is the IPv4 address book object client_net, the local internal tunnel endpoint is If2_ip (the server is on the If2 interface). A GRE tunnel called gre_to_clients is configured and the remote network is the address book object called client_net.GRE Tunnel
| Name | IP Address | Remote Endpoint | Remote Network |
|---|---|---|---|
| gre_to_clients | If2_ip | client_interface_ip | client_net |
Routes
Provided that the above GRE object has the option to automatically add routes enabled, the following route will be added by cOS Core to the main routing table.
| Network | Interface |
|---|---|
| client_net | gre_to_clients |
Services
| Name | Type | Destination Ports |
|---|---|---|
| mc_stream | udp | 1234 |
IP Rule Set Entries
| Entry Type | Source Interface |
Source Network |
Destination Interface |
Destination Network |
Service | Multiplex Interface |
|---|---|---|---|---|---|---|
| Multicast Policy |
If2 | If2_net | core | mc_group | mc_stream | gre_to_clients |
| IP Policy | If2 | If2_net | core | mc_group | mc_stream |
IGMP Rules
| Type | Action | Source Interface |
Source Network |
Multicast Group |
Multicast Source |
Relay Interface |
|---|---|---|---|---|---|---|
| Query | Proxy | If2 | If2_net | mc_group | all-nets | gre_to_clients |
| Report | Proxy | gre_clients | all-nets | all-nets | all-nets | If2 |
B. Client Side Configuration Setup
For the client side configuration, assume the server network is the IPv4 address book object server_net, the local internal tunnel endpoint is If3_ip (the clients are on the If3 interface). A GRE tunnel called gre_to_server is configured and the remote network is the address book object called server_net.GRE Tunnel
| Name | IP Address | Remote Endpoint | Remote Network |
|---|---|---|---|
| gre_to_server | If3_ip | server_interface_ip | server_net |
Routes
Provided that the above GRE object has the option to automatically add routes enabled, the following route will be added by cOS Core to the main routing table.
| Network | Interface |
|---|---|
| server_net | gre_to_server |
Services
| Name | Type | Destination Ports |
|---|---|---|
| mc_stream | udp | 1234 |
IP Rule Set Entries
| Entry Type | Source Interface |
Source Network |
Destination Interface |
Destination Network |
Service | Multiplex Interface |
|---|---|---|---|---|---|---|
| Multicast Policy |
gre_to_server | server_net | core | mc_group | mc_stream | If3 |
| IP Policy | gre_to_server | server_net | core | mc_group | mc_stream |
IGMP Rules
| Type | Action | Source Interface |
Source Network |
Multicast Group |
Multicast Source |
Relay Interface |
|---|---|---|---|---|---|---|
| Report | Proxy | If3 | If3_net | mc_group | all-nets | gre_to_server |
| Query | Proxy | gre_to_server | all-nets | all-nets | all-nets | If3 |