| Home Prev |  Virtual cOS Stream 4.00.00 Getting Started Guide Virtual cOS Stream 4.00.00 Getting Started Guide
|
Next |
|---|
Open vSwitch Installation
HA setup with KVM requires that Open vSwitch is installed on the Linux system. Open vSwitch will be used to provide virtual switches so that matching interfaces of the master and slave in the cluster can be connected together. The installation of Open vSwitch itself will not be discussed further here. Refer to the software's own documentation for help with installation.Open vSwitch is open source software that can be used in situations other than high availability to implement various networking solutions with KVM.
![[Note]](images/note.png) |
Note: The bridge-utils package must be removed |
|---|---|
|
Before installing Open vSwitch, the package bridge-utils must be removed from the Linux system. |
A Single Physical Server is Assumed
This section assumes that both the virtual firewalls in the HA cluster are installed on the same hardware server. In practice, two servers will probably be used for hardware redundancy and both will have KVM and Open vSwitch installed on them.The configuration of the connections between two separate servers will not be discussed in this section and it is up to the administrator to choose the most appropriate way of doing this. One approach is to use VLAN tagging with Open vSwitch so internal bridge traffic can pass between the physical servers that make up the HA cluster.
Setup
The initial setup of the two separate virtual firewalls is done as normal so they are initially working as separate firewalls. Before creating the HA cluster, it is necessary to first correctly configure the virtual networking to emulate the hardware connections that would normally be present between the master and slave units.Configuring Open vSwitch for HA
Assuming Open vSwitch has been installed, it is necessary to create separate virtual switches so that the pairs of matching interfaces from the firewalls in the cluster are connected together on each switch.This is done with the following steps:
A. Define an Open vSwitch bridge for each interface pair.
B. Configure the HA master and slave virtual machines to connect the interfaces to the relevant bridge.
These two steps are described next.
A. Define an Open vSwitch bridge for each interface pair.
Assuming that all of the default virtual interfaces (if1 and if2) on each firewall are to be connected together, two Open vSwitch bridges must be created:br1-internal - Connecting together the if1 interfaces. This is created using the Linux command:
[root@linux]# ovs-vsctl add-br br1-internal
br2-external - Connecting together the if2 interfaces and also connected to the public Internet via a physical interface called eth0 (this name will vary between configurations). This is created using the Linux commands:
[root@linux]# ovs-vsctl add-br br2-external [root@linux]# ovs-vsctl add-port br2-external eth0
B. Connect interface pairs to the relevant bridge.
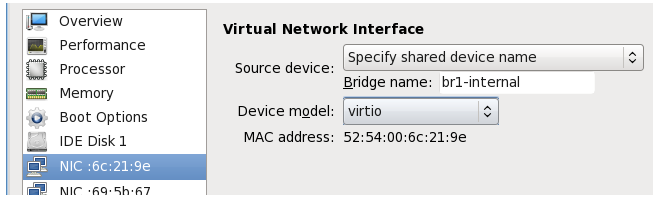
It is assumed that Virtual Machine Manager (virt-manager) will be used to configure each of the two virtual machines in the HA cluster.Assume that the interface if1 is to be associated with Open vSwitch bridge br1-internal on both master and slave firewalls. The intuitive approach is to select the NIC entry in the navigation menu that corresponds to the if1 interface and enter the Bridge name:
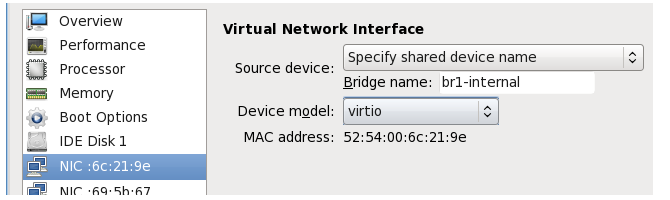
However, if this is now applied and the virtual machine started, it will give an error message:
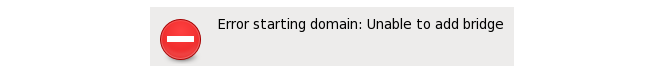
To get around this issue, allocate the Open vSwitch bridge using the following steps:
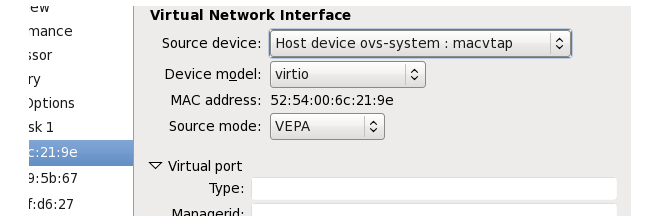
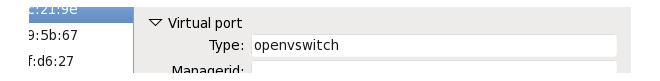
![[Note]](images/note.png) |
Note: Predefined bridges can simplify the above process |
|---|---|
|
An alternative to the above is much simpler but assumes that the network bridges have already been defined using virsh. If that is the case then the OVS bridges will be present in the virtual Machine Manager drop-down box.
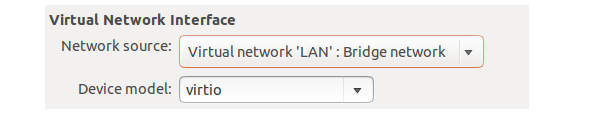
|
The networking for an HA cluster on a single hardware server is now complete. When the firewalls are on different servers, the procedure is similar. However, the administrator should then decide how they want to connect the Open vSwitch bridges on each server together. VLAN tagging can be used to separate the internal bridges on each server. Each pair of cluster interfaces uses a different VLAN ID to separate its traffic from the other pairs of interfaces.