| Home Prev |  cOS Stream 4.00.02 Administration Guide cOS Stream 4.00.02 Administration Guide
|
Next |
|---|
cOS Stream provides an additional type of VPN connection called SSL VPN. This makes use of the SSL/TLS protocol to provide a secure tunnel between a remote client computer and a network behind the Clavister NetShield Firewall.
SSL VPN is configured in cOS Stream by creating an SSLVPNServer object which listens for SSL/TLS client connections on all or specific Ethernet interfaces and provides client access to a specific local network behind the firewall. The SSLVPNServer object is itself treated as an interface in the firewall configuration and can be referenced like an interface by other configuration objects, such as an IPRule.
The typical SSL VPN scenario is illustrated in the diagram below where a client running SSL VPN software has access to hosts on a protected local network behind a firewall.
A primary advantage of SSL VPN is that it can provide an encrypted SSL/TLS tunnel for traffic between a client and a network behind a firewall, using readily available client software.A secondary advantage is that in many environments where roaming clients have to operate, such as hotels and airports, the network equipment may not allow another tunneling protocol like IPsec.
SSL VPN Client Software Requirements
The Clavister NetShield Firewall implementation of SSL VPN supports clients that are OpenVPN® compatible. A detailed discussion of client configuration is covered later in this section. (Legal notice: © 2002-2017 OpenVPN Inc. OpenVPN is a registered trademark of OpenVPN Inc.)Minimum Supported SSL/TLS Version
The minimum supported SSL/TLS version of connecting clients for the SSL VPN feature is TLS version 1.2.Summary of SSL VPN Setup Steps
SSL VPN setup requires the following configuration steps to be performed:Using SCP, upload the following certificates to cOS Stream:
A server certificate which will be sent to connecting SSL VPN clients during authentication. This consists of public and private key files.
Any certificate chain files which the client will need to authenticate the server certificate because it was signed by an intermediate CA.
One or more CA root certificate files which will be used to authenticate the certificate received from SSL VPN clients.
A Certificate object should be created in the firewall configuration for each of the uploaded certificates. The Type property for each object will be Local for the server certificate and Remote for the others.
The Certificate objects must be added as children of a CertificateStore object. The default store called ipsec could be used for this purpose but it is often better to create a new store and give it a name such as sslvpn. Any reference to a Certificate object must be qualified by the name of the store in which it is found. For example, sslvpn/my_ca_cert.
Set up User objects in a LocalUserDatabase which have the username and password of connecting SLL VPN clients. A new LocalUserDatabase might be created just to only hold SSL VPN client credentials.
Create an AuthenticationProfile object with its LocalUserDB property set to the database containing the credentials of the connecting clients.
Create an address book IP object which specifies a range of IP addresses. This will act as a pool of addresses which will be handed out to clients.
If client connections are only to be accepted from a specific IP range then define this range in an address book IP object.
Create an SSLVPNServer object and configure, at a minimum, the following mandatory properties:
LocalEndpoint - The IP of the outer tunnel endpoint to which clients connect.
ServerCert - The SSL server certificate sent to the client.
ServerIntermediateCert - Any certificate chain needed with the server certificate.
ClientCACert - The certificate sent by the client must be signed by this certificate.
AuthProfile - The previously defined AuthenticationProfile object.
LocalNetwork - The protected network clients are allowed to access.
ClientIPAddresses - The IP address range to hand out to clients.
IPAddress - The IP address of the inner local tunnel endpoint.
Other optional properties are discussed later in this section.
Ensure that a route exists that routes the LocalEndpoint IP address on the core interface. This will already exist as a predefined route if the LocalEndpoint is set to an interface's default IPv4 address object. For example, ip_if2 is already routed on core for the if2 interface.
Note that routes for client IPs will automatically be added as they connect and receive an IP address from the pool.
Create an IPRule object that will allow traffic from the SSLVPNServer interface to the protected network.
Make sure the SSL VPN client is correctly configured. Doing this is described next.
Configuring the VPN SSL Client
The following should be noted when configuring the SSL VPN client:A certificate must be installed in the client that can be authenticated by a CA root certificate configured in the firewall's SSLVPNServer object.
The client must be configured to connect to the LocalEndpoint IP address of the firewall's SSLVPNServer object.
The client needs to be configured to use a TUN device (not TAP) with either UDP or TCP. Note that the protocol selected must match the protocol allowed by the TransportProtocol property of the SSLVPNServer object.
Compression must be disabled as this is not supported by the firewall.
The TLS client mode should be used. The alternative of peer-to-peer is not currently supported.
The TLS extra-authentication option found in some clients is also not supported.
SSLVPNServer Object Properties
To configure SSL VPN, an SSLVPNServer object must be defined. The key object properties are as follows, divided up into mandatory and optional properties:Mandatory Properties
ClientIPAddresses
The pool of addresses from which client IP addresses are allocated. This is specified directly as an address range or as an address book object that specified a range. A private IP address range should be used for this purpose. All IPs must belong to the same network.
LocalEndpoint
The Ethernet interface IP address on which to listen for SSL VPN connection attempts by clients. This will typically be a public IPv4 or IPv6 address which will be initially accessed using a web browser across the public Internet.
LocalNetwork
The protected network that the clients will be allowed access to.
AuthProfile
The AuthenticationProfile object that will be used to authenticate the credentials of connecting users.
ServerCert
The Certificate object for the host certificate that will be sent to the client. The Type property of this object will be set to Local.
ClientCACert
The Certificate object for the CA root certificate that will validate the certificate sent by the client. The Type property of this object will be set to Remote.
More than one such Certificate object can be specified for this property as a comma separated list.
This is the IP address of the local endpoint inside the tunnel. This must be an IP address that belongs to the same network as the pool of addresses specified by the ClientIPAddresses property.
This IP address does not have to be explicitly excluded from the range specified by ClientIPAddresses. cOS Stream will automatically exclude the IPAddress value from the addresses handed out to connecting clients.
Optional Properties
DNS1 and DNS2
Up to two DNS server addresses can be specified which will be handed to a client when it connects for performing FQDN lookups. The DNS addresses can be specified as a raw IP address or as the name of an address book object.
ServerIntermediateCert
The Certificate object for any certificate chain. If the server certificate was signed by an intermediate CA, this needs to be also sent to the client so it can authenticate the server certificate.
More than one such Certificate object can be specified for this property as a comma separated list.
Note that an alternative to specifying the intermediate chain separately is to manually concatenate the chain file to the public key file of the server certificate before creating the Certificate object for the server certificate. However, this can only be done if the certificates are ASCII PEM encoded. If certificates are binary DER encoded they will have to be specified separately using this property.
RemoteEndpoint
This specifies the acceptable IP addresses of connecting clients. The default is all-nets (any IP).
TransportProtocol
This property can be set to a value of TCP, UDP or TCPUDP. The default value is TCPUDP which will allow either protocol to be used. Note that the value of this property must match the expected protocol settings of the connecting OpenVPN clients.
TCP has the advantage that it can function in almost all network environments, such as where a connection is being made via a public WiFi service. For example, in an airport. However, there will be a slight throughput overhead if TCP is used. UDP is preferable if there is a need to maximize throughput.
TCPPort
The TCP port on which the server is listening for incoming TCP connections. The default value is 443.
UDPPort
The UDP port on which the server is listening for incoming UDP connections. The default value is 1194.
SourceInterface
The interface or interfaces on which to listen for SSL VPN connections. If not specified it defaults to all interfaces. More than one interface can be specified by using an InterfaceGroup object.
Any interface can listen for SSL VPN connections, including VLAN interfaces.
ClientGeolocation
A GeolocationFilter can be specified so only connections coming from clients is a given geographical area will be accepted. The default is any-region.
ProxyARPInterfaces
A list of interfaces can be specified on which to ARP publish client IP addresses.
Usually, the only time that this option needs to be used is when the IP addresses assigned to clients are part of an already existing subnet that clients need access to. If that is the case, proxy ARP must be enabled for the interface connected to the subnet. If traffic is already correctly routed by cOS Stream, this is not needed.
LogEnabled
If enabled then client connections generate log messages. The default value is Yes.
KeepAliveInterval
The interval between keep-alive messages sent by the server. The default value is 10 seconds.
KeepAliveTimeout
The server will close a connection if no keep-alive messages are sent by the client for this amount of time. The default value is 120 seconds. The value of this setting should usually be greater than the KeepAliveInterval.
ReplayWindow
The size of the window used to store previous packet IDs to prevent a replay attack on the data channel. The value is expressed as the number of IDs to store. The default value is 512.
DataChannelCipher
The encryption algorithm used for the data channel. This defaults to AES-256-GCM.
ControlChannelCipher
The encryption algorithms for the control channel. This defaults to the following:
ECDHE-RSA-AES256-GCM-SHA384.
ECDHE-ECDSA-AES256-GCM-SHA384.
DHE-RSA-AES256-GCM-SHA384.
The complete list of SSLVPNServer object properties can be found in the separate CLI Reference Guide.
There are no restrictions on the use of IPv6 with SSL VPN in cOS Stream. Either IPv4 or IPv6 can be used for all the IP addresses when configuring SSL VPN. It also possible to have both, with all IPV6 outside the tunnel and all IPv4 inside the tunnel or the other way around.However, there may be restrictions imposed on IPv4 and IPv6 usage by the VPN client software selected and this should be checked by the administrator before configuring SSL VPN. The example below uses only IPv4 addresses.
Example 14.1. Configuring an SSL VPN Server
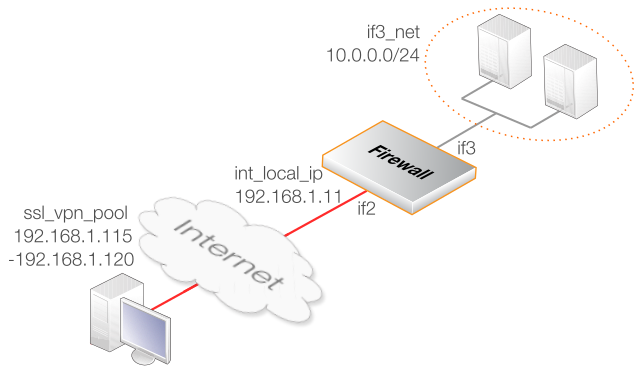
This example shows how to configure an SSL VPN server in cOS Stream that will provide secure access by connecting clients to a protected network behind the firewall.
The following assumptions are made:
The firewall's Ethernet interface if2 will be used to listen for client connections coming from the Internet and this has the public IPv4 address if2_ip. The address if2_ip is already routed on core so no route needs to be added for this.
Client connections will be made using SSL VPN to hosts located on the protected IPv4 network if3_net (10.0.0.0/24) connected to the firewall's if3 Ethernet interface.
The IPv4 addresses handed out to connecting clients will be come from the address range defined by the address book object ssl_vpn_pool which has the range 192.168.1.115 -> 192.168.1.120.
Only TCP connections will be allowed.
The internal local endpoint IPv4 address is 192.168.1.110 and this is defined by the address book object int_local_ip.
Authentication of client credentials will be performed against a new and separate local database of users that will be called ss_vpn_users.
A geolocation filter will be added so that connections will only be allowed from source IP addresses in a given location.
The appropriate SSL client software has been installed and configured correctly on the connecting client devices.
The diagram below illustrates the scenario which will be set up in this example.
Command-Line Interface
1. Upload the CA, server and any chain certificate files to the firewall using SCP.
2. Create Certificate objects for the uploaded files:
Create a CertificateStore for SSL VPN:
System:/> add CertificateStore sslvpnThen add the server's host certificate:System:/>cc CertificateStore sslvpnSystem:/CertificateStore/sslvpn>add Certificate ca_cert Type=Remote CertificateData=file://ca_cert.cer
System:/CertificateStore/sslvpn> add Certificate server_cert
Type=Local
CertificateData=file://server_cert.cer
PrivateKey=file://server_cert.keySystem:/CertificateStore/sslvpn> add Certificate server_cert_chain
Type=Remote
CertificateData=file://server_cert_chain.cerSystem:/CertificateStore/sslvpn>ccSystem:/>
3. Create a LocalUserDatabase and add at least one user:
System:/>add LocalUserDatabase ssl_vpn_usersSystem:/>cc LocalUserDatabase ssl_vpn_usersSystem:/LocalUserDatabase/ssl_vpn_users>add User client1 Password=someobscurepasswordSystem:/LocalUserDatabase/ssl_vpn_users>ccSystem:/>
4. Create an AuthenticationProfile object:
System:/> add AuthenticationProfile my_auth_profile
LocalUserDB=ssl_vpn_users5. Optionally create a GeolocationProfile object:
System:/> add GeolocationFilter my_geo_filter
Regions=EU
MatchUnknown=No6. Create an SSLVPNServer object:
System:/> add Interface SSLVPNServer my_sslvpn_server
TransportProtocol=TCP
AuthProfile=my_auth_profile
ClientCACert=sslvpn/ca_cert
ServerCert=sslvpn/server_cert
ServerIntermediateCert=sslvpn/server_cert_chain
LocalNetwork=if3_net
ClientIPAddresses=ssl_vpn_pool
LocalEndpoint=if2_ip
IPAddress=int_local_ip
SourceInterface=if2
RemoteEndpoint=all-nets-ip4
SourceGeolocation=my_geo_filter7. Create an IPRule for the traffic inside the tunnel:
System:/>cc RuleSet IPRuleSet mainSystem:/IPRuleSet/main>add IPRule Action=Allow Service=all_services SourceInterface=my_sslvpn_server SourceNetwork=all-nets-ip4 DestinationInterface=if3 DestinationNetwork=if3_net Name=ssl_to_if3
Providing Internet Access Via SSL VPN
It is possible to provide Internet access to clients through an SSL VPN tunnel. Using the setup in the example above as the starting point, assume that the firewall's if1 interface is connected to the Internet and the network all-nets is routed on this interface in the configuration. The following steps are needed to give Internet access to SSL VPN clients:Set the LocalNetwork of the SSLVPNServer to a value of all-nets (or in this case, all-nets-ip4 for IPv4 only access):
System:/> set Interface SSLVPNServer my_sslvpn_server
LocalNetwork=all-nets-ip4
Create an IPRule to allow traffic from the tunnel to flow to the Internet:
System:/>cc RuleSet IPRuleSet mainSystem:/IPRuleSet/main>add IPRule Action=Allow SourceInterface=my_sslvpn_server SourceNetwork=all-nets-ip4 DestinationInterface=if1 DestinationNetwork=all-nets-ip4 Service=all_services Name=ssl_to_internet
Ensure that there is a default route set up in the client that correctly routes Internet traffic into the SSL VPN tunnel. An existing default route may not do this. Some SSL VPN client software may have an option that will ensure all traffic is sent through the tunnel.
RateLimitCtrlChan
This is the maximimum number of packets per second allowed over the SSL control channel. Setting this to zero will remove any limit.
Default value: 50 packets/second
RateLimitWindowCtrlChan
This is the time window over which an average measurement is taken to estimate the control channel packet rate. The wider the window, the more likely that peaks and troughs in activity will be averaged out and the less likely that the RateLimitCtrlChan setting will be unnecessarily triggered.
Default value: 2 seconds
RekeyTransitionWindow
The number of seconds that an old key is valid after the rekey negotiation has begun.
Default value: 3600 seconds
How often rekeying is performed.
Default value: 3600 seconds
HandshakeTimeout
The maximum length of time allowed for a key exchange over the control channel.
Default value: 60 seconds