| Home Prev |  cOS Stream 4.00.06 Administration Guide cOS Stream 4.00.06 Administration Guide
|
Next |
|---|
The steps for setting up IPS are as follows:
Create any required SignatureGroup objects as children of the predefined IntrusionPrevention object. This will not be needed if the signatures to be used can be specified by category.
Add an IPSRule object as a child of the predefined IntrusionPrevention object to specify the traffic to be processed.
Add one or more IPSRuleAction objects to the rule which specify:
The IPS signatures to be used when scanning the traffic targeted by the rule. This can be done by specifying one or more signature categories and/or specifying one or more SignatureGroup objects. If both a category and a group is specified then a logical OR is used in combining them.
The action to take when a signature triggers. As described previously, this can be one of of Protect (the default), Audit or Ignore.
At least one IPS signature file must be activated. Doing this is described in Section 27.3, IPS Signature Management.
Example 27.1. Setting up IPS for HTTP Server Protection
The following example details the steps needed to set up IPS for a simple scenario where an HTTP server is exposed to the Internet on the DMZ network with a public IPv4 address. The public Internet can be reached through the firewall on the WAN interface as illustrated below.
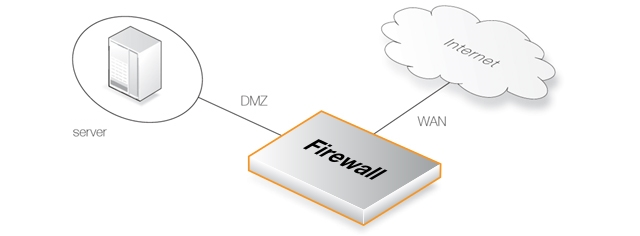
An IPSRule object called srv_rule will be created with the Service set to http. The SourceInterface and SourceNetwork defines where traffic is coming from, in this example the external network. The DestinationInterface and DestinationNetwork define where traffic is directed to, in this case the server.
Command-Line Interface
Change the context to be the IntrusionPrevention object which is predefined:
System:/>cc IntrusionPreventionSystem:/IntrusionPrevention>
Create a signature group for the signature as a child:
System:/IntrusionPrevention>
add IPSSignatureGroup my_group
IncludeCategory=IPS_WEB_*
Create a rule as a child:
System:/IntrusionPrevention>
add IPSRule
SourceInterface=wan
SourceNetwork=wan_net
DestinationInterface=dmz
DestinationNetwork=http_server_ip
Service=http
Name=srv_rule
Added IPSRule/1(srv_rule)Note that the Name property is optional.
Change the CLI context to be the rule:
System:/IntrusionPrevention>cc IPSRule 1(srv_rule)System:/IntrusionPrevention/IPSRule/1(srv_rule)>
Add the action as a child, including the group defined earlier:
System:/IntrusionPrevention/IPSRule/1(srv_rule)>
add IPSRuleAction
Action=Protect
SignatureGroup=my_groupNote that the default action is Protect but it is included above for clarity.
Example 27.2. IPS Category Filtering Setup with Ignored Signatures
This example is similar to the previous but this time flows will be dropped if any signatures in the category IPS_WEB_POLICY are triggered. However, the vendor signature with the SID 64317, which is part of the IPS_WEB_POLICY category, will be an exception and will only cause a log message to be generated if it triggers.
To achieve this, two IPSRuleAction objects will be created. The first will trigger on the SID 64317 and the action taken will be Audit. The second will trigger on the category IPS_WEB_POLICY and the action will be Protect.
Command-Line Interface
Change the context to be the IntrusionPrevention object:
System:/>cc IntrusionPreventionSystem:/IntrusionPrevention>
Create a child signature group for the SID 64317 exception:
System:/IntrusionPrevention>
add IPSSignatureGroup my_sig_exception
IncludeVendorSignature=64317
Add a single rule for the targeted traffic:
System:/IntrusionPrevention>
add IPSRule
SourceInterface=wan
SourceNetwork=wan_net
DestinationInterface=dmz
DestinationNetwork=http_server_ip
Service=http
Name=srv_rule
Added IPSRule/1(srv_rule)
Change the CLI context to be the rule:
System:/IntrusionPrevention>cc IPSRule 1(srv_rule)System:/IntrusionPrevention/IPSRule/1(srv_rule)>
Add an action so that SID 64317 is logged but not dropped:
System:/IntrusionPrevention/IPSRule/1(srv_rule)>
add IPSRuleAction
Action=Audit
SignatureGroup=my_sig_exception
Add a second action so flows that trigger the IPS_WEB_POLICY category (with the exception of SID 64317) are dropped:
System:/IntrusionPrevention/IPSRule/1(srv_rule)>
add IPSRuleAction
Action=Protect
SignatureCategory=IPS_WEB_POLICYNote that the default action is Protect but it is explicitly stated above for clarity.
Example 27.3. Setting an IPS Scan Limit
This example shows how an IPS scan limit of 2048 bytes can be set in the IPSRule from the previous example.
Command-Line Interface
From the previous example, add a single rule for the targeted traffic:
System:/IntrusionPrevention>
add IPSRule
SourceInterface=wan
SourceNetwork=wan_net
DestinationInterface=dmz
DestinationNetwork=http_server_ip
Service=http
Name=srv_rule
ScanLimit=Yes
ScanLimitBytes=2048
Added IPSRule/1(srv_rule)