| Home Prev |  cOS Stream 4.00.06 Administration Guide cOS Stream 4.00.06 Administration Guide
|
Next |
|---|
The GPRS Tunneling Protocol (GTP) is a communication protocol used to carry data between telecom networks. The GTP Inspection feature in cOS Stream provides the ability to apply a range of integrity checks to GTP traffic. Specifically, it protects the P-GW in an LTE/4G network (or the GGSN in a GPRS/3G network) when a S-GW (or SGSN) is communicating with the P-GW (or GGSN) over an untrusted network like the Internet.
The remote interface behind which the firewall sits to inspect traffic is known as the S8 interface in LTE/4G networks (the Gp interface in 3G networks). GTP inspection examines the traffic passing through this interface as it flows between a visited (remote) network and the home (local) network.
Naming Conventions
For convenience, the rest of this section will use only the LTE/4G naming conventions. The naming of object properties within the firewall CLI interface also uses only LTE/4G naming conventions. However, all the principles described can be applied to 3G networks.In an LTE/4G network, the S-GW side will be referred to as the downlink (or user) side and the P-GW side will be referred to as the uplink (or network) side. The terms downlink and uplink are used by the firewall's CLI.
GTP Inspection Features
The GTP inspection feature in cOS Stream provides a defense against the following kinds of potential security threats:Malformed GTP traffic. This can include IE manipulation, missing information elements, invalid values, invalid header or IE's structure.
Request/response mismatches.
Raw data traffic causing a denial of service.
GTP inside GTP. This could result in traffic reaching nodes in the core network that should be inaccessible to roaming partners.
The following methods are used by GTP inspection to protect against the threats listed above:
GTP-C/U message validation.
GTP-C/U session tracking. This only allows GTP-U traffic to be forwarded for established GTP-U bearers.
State tracking for some GTP-C message types (but not GTP-U types).
GTP-in-GTP detection for GTP-U tunneled traffic.
In addition, the administrator can set the following limits in the GTP inspection feature:
GTP session and bearer timeout values.
The maximum number of GTP sessions and bearers allowed.
GTP messaging using either UDP with IPv4 or UDP with IPv6 is supported.
The tunneled GTP traffic can be either IPv4 or IPv6.
GTP in GTP tunnel detection will function regardless of the IP protocols used.
Steps For GTP Inspection Setup
The following steps are required to set up GTP inspection:Define a new GTPInspectionProfile object that is configured to perform the required checks on GTP traffic. This same profile can be used for both traffic directions as well as being used across multiple IP rules.
Define IPRule objects that trigger on each direction of traffic flow and associate the GTPInspectionProfile object from the previous step with the GTPInspectionProfile property of both rules.
The service associated with the IP rules should either be the predefined service object called gtpc-udp or a similar administrator defined service object.
DownlinkSourceInterface
The allowed source interface(s) for GTP-U traffic originating from the SGSN/S-GW.
DownlinkNetwork
An S-GW address filter for GTP-U traffic.
UplinkSourceInterface
The allowed source interface(s) for GTP-U traffic originating from the GGSN/P-GW.
UplinkNetwork
A P-GW address filter for GTP-U traffic.
All the properties for the GTPInspectionProfile object are listed in the separate CLI Reference Guide.
Specifying the GTP Version
The optional property GTPVersion specifies the allowed GTP version or versions. The default value is GTPv2 and this should be used for LTE scenarios. The value can be specified as GTPv1 instead or both versions can be allowed by specifying GTPv1,GTPv2.Sessions Maximums are Cumulative Per Profile
It should be noted that the property MaxSessions, like all the other session maximum properties, apply to the cumulative sessions for a single GTPInspectionProfile object. This is true, regardless of how many IPRule objects reference the object.The following is a list of all the session maximum properties:
MaxSessions
The maximum number of concurrent GTP-C sessions allowed by the profile object. The default value is 1024.
MaxSessionsPerSourceIP
The maximum number of concurrent GTP-C sessions allowed for each unique source IP address. The default value is 1024.
MaxBearersPerSession
The maximum number of bearers allowed for each GTP-C session. The default value is 16.
Example 19.1. Setting Up GTP Inspection for LTE
This example shows how GTP inspection can be set up for traffic flowing between the S-GW and the P-GW in an LTE scenario.
As illustrated in the diagram below, it is assumed that the S-GW's network s_gw_net is connected to the firewall's if1 interface and the P-GW's network p_gw_net is connected to the if2 interface. It is also assumed that both the S-GW and P-GW are using the default ports of 2123 for GTP-C and 2152 for GTP-U.
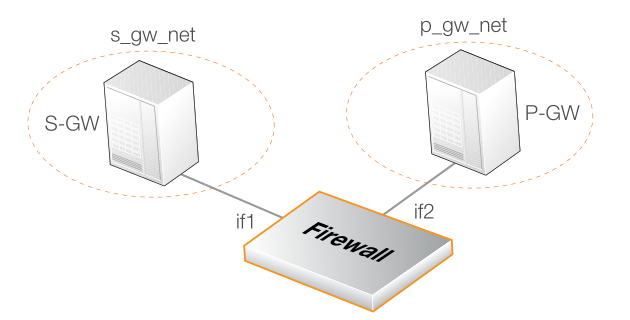
Note that the GTP version will be explicitly specified in this example for clarity, even though it defaults to the required value of GTPv2 for LTE.
Command-Line Interface
A. Define a new GTPInspectionProfile:
System:/> add GTPInspectionProfile my_s8_profile
GTPVersion=GTPv2
DownlinkSourceInterface=if1
DownlinkNetwork=s_gw_net
UplinkSourceInterface=if2
UplinkNetwork=p_gw_netB. Define an IPRule that allows GTP-C traffic to the P-GW:
System:/>cc RuleSet IPRuleSet mainSystem:/IPRuleSet/main>add IPRule Action=Allow Service=gtpc-udp SourceInterface=if1 SourceNetwork=s_gw_net DestinationInterface=if2 DestinationNetwork=p_gw_net Name=my_gtp_uplink_rule GTPInspectionProfile=my_s8_profile
C. Define an IPRule that allows GTP-C traffic from the P-GW:
System:/>cc RuleSet IPRuleSet mainSystem:/IPRuleSet/main>add IPRule Action=Allow Service=gtpc-udp SourceInterface=if2 SourceNetwork=p_gw_net DestinationInterface=if1 DestinationNetwork=s_gw_net Name=my_gtp_downlink_rule GTPInspectionProfile=my_s8_profile
System:/> gtpinspection -show=brief
Active GTP-C Sessions
ID Age Orig Term
-- --- ---------------------------- -----------------------------
1 92 if2:192.168.20.210:2123:0x7a if2:192.168.20.220:2123:0x443
2 79 if2:192.168.20.210:2123:0x87 if2:192.168.20.220:2123:0x451
Version Bearers
-------- -------
GTP-C v2 1
GTP-C v2 1Many filtering options exist to limit the scope of the output. For example, the following command would show the activity for only the GTPInspectionProfile object called my-gtp-profile.:
System:/> gtpinspection -show -profile=my-gtp-profile
The -close option can be used to close the current sessions on a particular profile or all profiles. For example, the following command will close all active GTP sessions currently active through the profile object called my-gtp-profile:
System:/> gtpinspection -close -profile=my-gtp-profileClosing a flow can be useful where there is a need to force the GTP endpoints to reestablish sessions and bearers.
The full list of gtpinspection command options can be found in the separate CLI Reference Guide.
The gtpinspection command also has a -snoop option which allows GTP interactions and traffic to be monitored in real time with details of GTP interactions displayed on the console as they occur. The snooping option must be first enabled and then left to run. For example, the following command would enable snooping for the profile object called my-gtp-profile and might result in the accompanying output:System:/> gtpinspection -snoop=brief -profile=my-gtp-profile
Setting GTP snoop level to 'brief' with filter:
profile=my-gtp-profile origiface=any
origip=0.0.0.0/0,::/0 termip=0.0.0.0/0,::/0
SNOOP: my-gtp-profile : <UDP if2;192.168.20.21:2123 -> 192.168.20.22:2123>
<UDP if2;192.168.20.22:2123 -> 192.168.20.21:2123>, Type: Echo requestSystem:/> gtpinspection -snoop=full -profile=my-gtp-profile
Setting GTP snoop level to 'full' with filter:
profile=my-gtp-profile origiface=any
origip=0.0.0.0/0,::/0 termip=0.0.0.0/0,::/0
SNOOP: GTPINSPECTION-2 : if1:192.168.20.21:2123 ->
if2:192.168.20.22:2123
GTP Version: GTPv2-C
Type: Create Session Request (32)
Length: 124
TEID: 0x0
IE (Information Elements): 9
IMSI: 2400100
MSISDN: 466609700000
RAT Type: EUTRAN (WB-E-UTRAN) (6)
F-TEID: (TEID: 0x3c8, Ifacetype: 6, 192.168.20.21)
APN: test
Bearer Context:
IE (Grouped): 3
EBI: 5
Bearer Level Quality of Service:
F-TEID: (TEID: 0x3cd, Ifacetype: 4, 192.168.20.22)
PDN Type:
PAA: 10.10.3.200
Recovery: 1System:/> gtpinspection -snoop=off