| Home Prev |  cOS Stream 4.00.06 Administration Guide cOS Stream 4.00.06 Administration Guide
|
Next |
|---|
Overview
DNS queries can provide a means of attack for malicious third parties. The DNS ALG feature can be used to monitor DNS queries as they flow through the firewall in the following scenarios:DNS queries flowing to the public Internet from protected clients behind the firewall.
DNS queries being sent, usually from the Internet, to a DNS server located on a DMZ behind the firewall.
Setting up the DNS ALG
Deploying the DNS ALG requires the following steps:Define a DNSAlgProfile object that describes the DNS connection. DNSAlgProfile object properties are described later in this section.
A predefined DNSAlgProfile object is provided called dns which has default settings. However, this object cannot be edited and a custom DNSAlgProfile object with customized settings may provide better security.
Define an IPRule object for the targeted traffic. This rule must have the following two properties correctly set in order to use the DNS ALG:
Service - This should be a Service object that targets the DNS traffic. A predefined service object is provided called dns-all or the predefined objects dns-udp and dns-tcp to target UDP and TCP DNS traffic. A custom service could be used instead. One service object can be shared across multiple IP rules.
Any Service object used with DNS must have its AppProto property set to the value DNS. If this is not the case, the DNS ALG will not be applied to a flow even though it is configured in an IP rule. This AppProto property is already correctly set for the predefined service objects, such as dns-all.
DNSAlgProfile - This must be set to the DNSAlgProfile object that was defined above or it can be set to the predefined object called dns. One DNSAlgProfile object can be shared across multiple IP rules.
MaxSessions
This is the maximum number of DNS sessions allowed for this DNSAlgProfile object. Multiple IP rules could use the same DNSAlgProfile object so the total sessions across all these IP rules could not be more than the MaxSessions value for the shared object.
MaxUDPQueryLength
The maximum allowed payload size in bytes for UDP DNS queries. The default value is 512. Queries exceeding this size will be dropped and a log message generated.
MaxUDPResponseLength
The maximum allowed payload size in bytes for UDP DNS responses. The default value is 512. Responses exceeding this size will be dropped and a log message generated. When using DNSSEC the responses can be large so the default value should be increased.
MaxTCPQueryLength
The maximum allowed payload size in bytes for TCP DNS queries. The default value is 4096. Queries exceeding this size will be dropped and a log message generated.
MaxTCPResponseLength
The maximum allowed payload size in bytes for TCP DNS responses. The default value is 4096. Responses exceeding this size will be dropped and a log message generated. When using DNSSEC the responses can be large so the default value should be increased.
RecursionDesiredFlag
DNS recursion means that a DNS server can query other servers to fully resolve the original query. DNS requests have a Recursion Desired (RD) flag which is typically set by, for example, client browsers.
The RecursionDesiredFlag property is enabled by default in the DNS ALG so requests with the RD flag set are allowed. However, recursion could be used as a means to launch an amplification attack against a DNS server by sending fake DNS queries from a spoofed IP address and the RecursionDesiredFlag property can be enabled to drop any DNS queries with the RD flag set.
MaxQuestionEntries
The maximum number of question entries in a query. The default value is 1.
AllowedClasses
This property is set to a list of the allowed classes. Classes can be specified either as their numeric ID or their name (tab completion will show names and IDs). The default value is IN (the Internet class). The value <All> can be used to specify all classes.
AllowedTypes
This property is set to a list of the allowed types. Types can be specified either as their numeric ID or their name (tab completion will only show names). For example:
System:/> set DNSAlgProfile my_dns_profile
AllowedTypes=A,CNAME,NS,OPT
The default value for this property is <All> (all types are allowed).
Translations
To enable DNS translation, this property should be set to an instance of the DNSTranslationList object. The default value is <disable> (no translation).
TranslationOnDNSSEC
If DNS translation is enabled, force addresses to be modified even if a DNS packet is digitally signed using DNSSEC. This will invalidate the DNSSEC signature but can still be useful for clients that do not perform validation.
ScrambleQueryID
When enabled (the default) the transaction ID of DNS queries are randomized. This helps defend against cache poisoning caused by the spoofing of DNS queries using non-randomized IDs.
State Tracking is Always Enabled
The DNS ALG has state tracking always enabled and there is no setting to control this. State tracking means that DNS queries and responses are matched to each other. A response with no matching query is automatically dropped.Forms of DNS Attack and DNS ALG Defense Mechanisms
The DNS ALG is designed to provide a defense against the following forms of DNS attack:DNS Cache Poisoning
DNS cache poisoning relies on being able to spoof DNS responses, which means it is mainly applicable to DNS traffic over UDP. An attacker forges and sends a fake/spoofed response to a legitimate DNS query. If the DNS client that sent the original query accepts the faked response, this allows the attacker to inject false entries into the client's DNS cache. The DNS ALG will protect against this in multiple ways. For example, by using the ScrambleQueryID property of the DNSAlgProfile object (making it more difficult for an attacker to generate a proper response) and also through query/response state tracking (which drops unexpected responses and is always enabled).
In addition, the RecursionDesiredFlag property of the DNSAlgProfile object can be used to prevent DNS clients from sending queries which request recursion.
DNS Reflection/Amplification Attacks
In this scenario, a DNS server is used to reflect and/or amplify traffic. An attack can be performed in different ways but generally relies on UDP for the spoofing of the source address of the attack victims. An attacker will generate a large amount of DNS queries to one or more DNS servers which will all respond to the spoofed address. Typically, the attacker will craft the spoofed DNS queries in a way that they will not only reflect, but also amplify traffic (for example, by asking many questions in a single query).
The DNS ALG can help protect against this using the following DNSAlgProfile object properties:
DNS Tunneling
In this scenario, an attacker uses DNS traffic to tunnel data through the firewall. The DNS ALG provides protection against basic tunneling by only allowing well-formed DNS traffic through. This means that cOS Stream validates the DNS traffic against the protocol description in the relevant RFCs. Non-conforming data traffic will be dropped.
More sophisticated tunneling attacks might encode data as valid domain names and store it in the DNS queries/responses. This is difficult to detect. The DNS ALG provides a degree of protection against this using the following DNSAlgProfile object properties:
DNS Translation
The DNS ALG can provide DNS translation to convert the result of a DNS query from one specific IP address to another. A typical use case for this feature is where the public IP address for a server returned by a DNS server should be translated to its private IP address for internal clients.To implement IP translations, the steps are as follows:
Create a new DNSTranslationList object.
Add one or more DNSTranslation objects as children to the parent DNSTranslationList object.
Create a DNSAlgProfile object for the DNS traffic and set its DNSTranslationList property to the list created in the previous steps. The predefined DNSAlgProfile object called dns could be used but this is not recommended.
Create an IPRule object that targets the DNS traffic and set its DNSAlgProfile property to the profile created in the previous step.
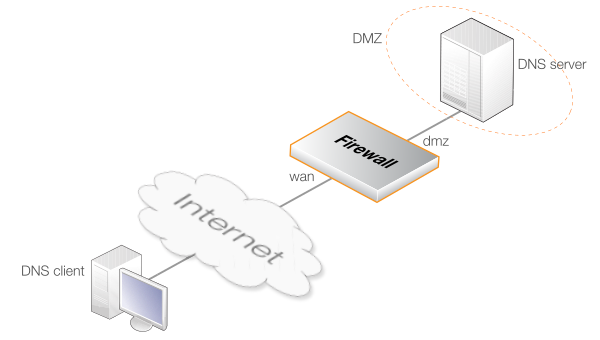
Example 10.5. Using the DNS ALG with an Internal DNS Server
In this example, the DNS ALG is used to filter UDP DNS queries sent to a protected DNS server on a DMZ which are coming from the Internet. This is illustrated in the diagram below.
Command-Line Interface
Change the current CLI context to be the main IP rule set:
System:/> cc RuleSet IPRuleSet mainCreate a SAT IP rule that uses the predefined DNS ALG profile:
System:/IPRuleSet/main> add IPRule
SourceInterface=wan
SourceNetwork=all-nets-ip4
DestinationInterface=core
DestinationNetwork=wan_ip
Service=dns-udp
Action=Allow
DestinationTranslation=SAT
SetDestinationAddress=Offset
NewDestinationIP4=10.0.0.5
DNSAlgProfile=dns
Name=SAT_DNS_To_DMZNow, return to the default CLI context if no more rules are needed:
System:/IPRuleSet/main>ccSystem:/>
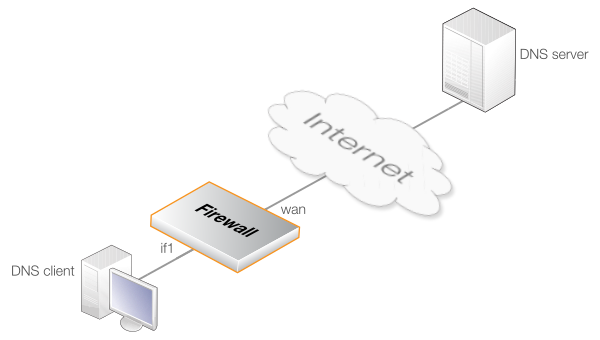
Example 10.6. Using the DNS ALG with Protected Clients
In this example, clients on the internal protected network if1_net are sending DNS queries out to the public Internet using NAT via the interface wan. This is illustrated in the diagram below.
A single translation will be applied that changes a DNS server response so that the IPv4 address 203.0.113.10 will be changed to 10.0.0.10.
Create a DNSTranslationList object:
System:/> add DNSTranslationList my_translationsAdd DNSTranslation objects to the list:
Change the CLI context to the list:
System:/> cc DNSTranslationList my_translationsAdd the translation:
System:/DNSTranslationList/my_translations> add DNSTranslation
FromIP=203.0.113.10
ToIP=10.0.0.10Return to the default CLI context:
System:/DNSTranslationList/my_translations>ccSystem:/>
Create a custom DNSAlgProfile using the list:
System:/> add DNSAlgProfile my_dns_alg Translations=my_translations
Create an IPRule that uses the profile:
Change the CLI context to be the main IP rule set:
System:/> cc RuleSet IPRuleSet mainCreate the IP rule:
System:/IPRuleSet/main> add IPRule
SourceInterface=if1
SourceNetwork=if1_net
DestinationInterface=wan
DestinationNetwork=all-nets-ip4
Service=dns-udp
Action=Allow
DNSAlgProfile=my_dns_alg
SourceTranslation=NAT
SetSourceAddress=InterfaceAddress
Name=NAT_DNS_to_Internet