| Home Prev |  cOS Stream 4.00.06 Administration Guide cOS Stream 4.00.06 Administration Guide
|
Next |
|---|
Overview
File Transfer Protocol (FTP) is a TCP/IP-based protocol for exchanging files between a client and a server. The client initiates the connection by connecting to the FTP server. Normally the client needs to authenticate itself by providing a predefined login and password. After granting access, the server will provide the client with a file/directory listing from which it can download/upload files (depending on access rights). The FTP ALG provides a way to inspect and control FTP flows, providing better security. FTP modes of operation and the protocol's security issues will be discussed next, before moving on to how the FTP ALG is configured.FTP Channels
FTP uses two communication channels, one for FTP control commands and one for the actual files being transferred. When an FTP session is opened, the FTP client establishes a TCP connection (the control channel) to port 21 (by default) on the FTP server. What happens after this point depends on which of two FTP modes is being used. These modes are explained next.FTP Connection Modes
FTP operates in two modes: active and passive. These determine the role of the server when opening data channels between client and server.Active Mode
In active mode, the FTP client sends a command to the FTP server indicating what IP address and port the server should connect to. The FTP server establishes the data channel back to the FTP client using the received address information.
Passive Mode
In passive mode, the data channel is opened by the FTP client to the FTP server, just like the command channel. This is often the recommended default mode for FTP clients although sometimes the opposite may be recommended.
FTP Modes and Security Issues
Let us look at FTP flows between a client and server when an FTP ALG is not used and only IP rules control the flows. Both active and passive modes of FTP operation can present issues for cOS Stream in this situation. Consider a scenario where an FTP client on an internal network connects through a Clavister NetShield Firewall to an FTP server out on the Internet. An IP rule must be configured to allow network traffic from the protected FTP client to port 21 on the public FTP server.When active mode is used, cOS Stream does not know that the FTP server will establish a new connection back to the FTP client. Therefore, the incoming connection for the data channel from the server will be dropped. As the port number used for the data channel is dynamic, the only way to solve this is to allow traffic from all ports on the FTP server to all ports on the FTP client. Obviously, this is not a good solution.
When passive mode is used, cOS Stream does not need to allow connections from the FTP server. On the other hand, cOS Stream still does not know what port the FTP client will try to use for the data channel. This means that it has to allow traffic from all ports on the FTP client to all ports on the FTP server. Although this is not as insecure as in the active mode case, it still presents a potential security threat. Furthermore, not all FTP clients are capable of using passive mode.
The FTP ALG Solution
The FTP ALG handles these issues by fully reassembling the TCP stream of the FTP command channel and examining its contents. By doing this, cOS Stream knows what port to open for the data channel. Furthermore, the FTP ALG also provides functionality to filter out certain control commands and provide buffer overrun protection.FTP Commands Supported by the FTP ALG
The following are known FTP commands that are supported by the ALG:
Unsupported FTP Commands
Some FTP commands are unsupported and will never be allowed by the FTP ALG, even if the AllowUnknownCommands setting is enabled (it is disabled by default).The following commands will always be unrecognized and will result in an illegal_command_received log message being generated:
The following encryption related commands will always be unrecognized and will result in an unsupported_encryption_command_rejected log message being generated:
Any command that is not in the above unsupported command lists, or in the list of supported commands, will be treated as an unknown command and will be allowed if the AllowUnknownCommands setting is enabled.
Setting up the FTP ALG
Deploying the FTP ALG requires the following steps:Define an FTPAlgProfile object that describes the FTP connection. FTPAlgProfile object properties are described later in this section.
cOS Stream provides a predefined FTPAlgProfile object called ftp-passthrough which has the default settings. However, this object cannot be edited and a custom FTPAlgProfile object with customized settings may provide better security.
Define an IPRule object for the targeted traffic. This rule must have the following two properties correctly set in order to use the FTP ALG:
Service - This should be a Service object that targets the FTP traffic. cOS Stream provides a predefined service called ftp to do this. A custom service could also be used in its place. One service object can be shared across multiple IP rules.
Any Service object used with FTP must have its AppProto property set to the value FTP. If this is not the case, the FTP ALG will not be applied to a flow even though it is configured in an IP rule. This AppProto property is already correctly set for the predefined ftp service.
FTPAlgProfile - This must be set to the FTPAlgProfile object that was defined above or it can be set to the predefined object called ftp-passthrough. One FTPAlgProfile object can be shared across multiple IP rules.
ServerPorts
The list of server ports that are acceptable.
ClientPorts
The list of client ports that are acceptable.
MaxSessions
This is the maximum number of FTP sessions allowed for this FTPAlgProfile object. Multiple IP rules could use the same FTPAlgProfile object so the total sessions across all these IP rules could not be more than the MaxSessions value for the shared object.
The default value of the predefined ftp-passthrough object is 1000 concurrent sessions.
AllowUnknownCommands
This property allows commands that the ALG does not consider part of the standard set. It is disabled by default. The commands allowed are any that are not explicitly never allowed. Commands that are never allowed are listed earlier in this section.
![[Note]](images/note.png) |
Note: Some FTP commands are never allowed |
|---|---|
|
Some commands, such as encryption instructions, are never allowed. Encryption would mean that the FTP command channel could not be examined by the ALG and the dynamic data channels could not be opened. |
MaxLineLength
This is the maximum line length in the control channel. Creating very large control channel commands can be used as a form of attack against a server by causing buffer overruns This restriction combats this threat. The default value is 256.
If very long file or directory names on the server are used then this limit may need to be raised. The shorter the limit, the better the security.
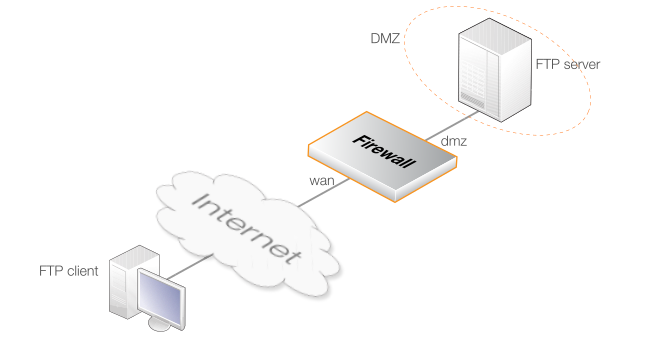
Example 10.1. Protecting an Internal FTP Server
In this example, an FTP server is located on a DMZ with a private IPv4 address of 10.10.10.5, as shown below. FTP clients on the Internet will access the server via the wan interface which has a public IP address. An IP rule needs to be created that translates client requests to the FTP server's address using SAT.
Command-Line Interface
Change the CLI context to be the main IP rule set:
System:/> cc RuleSet IPRuleSet mainCreate a SAT IP rule:
System:/IPRuleSet/main> add IPRule
SourceInterface=any
SourceNetwork=all-nets-ip4
DestinationInterface=core
DestinationNetwork=wan_ip
Service=ftp
Action=Allow
FTPAlgProfile=ftp-passthrough
DestinationTranslation=SAT
SetDestinationAddress=Offset
NewDestinationIP4=10.10.10.5
Name=SAT_FTP_to_DMZ
Note that further IP rules will be needed if protected clients on internal networks are to be allowed to also access the FTP server. Doing this is described in Example 9.8, “Enabling Traffic to a Protected Web Server in a DMZ (1:1)”.
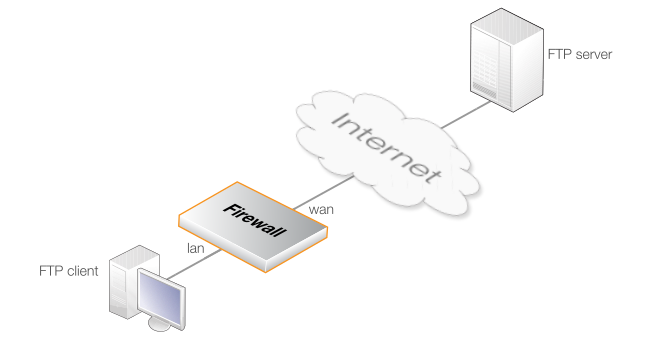
Example 10.2. Protecting Internal FTP Clients
In this example, protected internal clients are connecting to FTP servers on the Internet. It is assumed that the clients have private IPv4 addresses and NAT is used so they share a single public IPv4 address.
Change the CLI context to be the main IP rule set:
System:/> cc RuleSet IPRuleSet mainCreate the IP rule:
System:/IPRuleSet/main> add IPRule
SourceInterface=if1
SourceNetwork=if1_net
DestinationInterface=wan
DestinationNetwork=all-nets-ip4
Service=ftp
Action=Allow
FTPAlgProfile=ftp-passthrough
SourceTranslation=NAT
SetSourceAddress=InterfaceAddress
Name=NAT_FTP_to_Internet