| Home Prev |  cOS Core 15.00.02 Administration Guide cOS Core 15.00.02 Administration Guide
|
Next |
|---|
ZoneDefense Blocks Hosts or Networks Using Switches
ZoneDefense is a feature that can be used as a counter-measure to stop a threat-infected computer in a local network from infecting other computers.When hosts or clients in a network become infected with a virus or another form of threat, this can often show its presence through anomalous behavior, such as large numbers of new connections being opened to outside hosts. With the ZoneDefense feature, cOS Core can automatically instruct a D-Link switch to block access to a host or network when such unusual behavior is detected.
The ZoneDefense feature will only function with switches manufactured by D-Link and a list of the supported switches is given later in this section.
ZoneDefense Makes Use of SNMP
Simple Network Management Protocol (SNMP) is an application layer protocol for complex network management. SNMP allows the managers and managed devices in a network to communicate with each other.For ZoneDefense, cOS Core uses SNMP to control switch behavior. Management privileges to a switch are gained by cOS Core using the configured SNMP Community String for write access. The appropriate Management Information Base (MIB) file is then used by cOS Core to determine how commands should be sent to a switch.
All relevant MIB files are already loaded into cOS Core but when configuring ZoneDefense, cOS Core needs to be told which MIB to use. For older D-Link switches this is done by specifying the exact switch product name. However, newer D-Link switches use a common Universal MIB so the exact switch type need not be specified.
Threshold Rules Can Trigger ZoneDefense
By setting up Threshold Rule in cOS Core, hosts or networks that are exceeding a defined connection threshold can be dynamically blocked using the ZoneDefense feature. Thresholds are based on either the number of new connections made per second, or on the total number of connections being made.These connections may be made by either a single host or all hosts within a specified CIDR network range (an IP address range specified by a combination of an IP address and its associated network mask). These rules are discussed further in Section 7.9, Threshold Rules.
Botnet Protection Can Trigger ZoneDefense
The Botnet Protection feature in cOS Core can trigger ZoneDefense when the source or destination IP for a connection on any interface is flagged as being associated with a botnet by the IP reputation subsystem. This feature is described further in Section 7.3, Botnet Protection.Blocking Uses ACL Uploads
When cOS Core detects that a host or a network has reached the specified threshold limit, it uploads Access Control List (ACL) rules to the relevant switch and this blocks all traffic for the host or network that is displaying the unusual behavior. Blocked hosts and networks remain blocked until the system administrator manually unblocks them using the Web or Command Line interface. Every switch that is to be controlled by the firewall has to be manually specified in the cOS Core configuration.The information that must be specified in the configuration setup in order to control a switch includes:
The IP address of the management interface of the switch.
The switch model type (or Universal MIB for newer switches).
The SNMP community string for write access to the switch.
ZoneDefense supports all newer D-Link switches which use the Universal MIB. The following is a list of supported switches:
![[Tip]](images/tip.png) |
Tip: Switch firmware versions should be the latest |
|---|---|
|
It is advisable when using ZoneDefense to make sure that all switches have the latest firmware version installed. |
Using Threshold Rules
A threshold rule will trigger ZoneDefense to block out a specific host or a network if the connection limit specified in the threshold rule is exceeded. The triggering limit can be one of two types:Connection Rate Limit
This can be triggered if the rate of new connections per second to the firewall exceeds a specified threshold.
Total Connections Limit
This can be triggered if the total number of connections to the firewall exceeds a specified threshold.
Threshold rules have a traffic filter which are similar to other cOS Core rules. This filter specifies what type of traffic a threshold rule applies to.
A single threshold rule object has the following properties:
Traffic that matches the above criteria and causes the host/network threshold to be exceeded will trigger the ZoneDefense feature. This will prevent the host/networks from accessing the switch(es). All blocking in response to threshold violations will be based on the IP address of the host or network on the switch(es). When a network-based threshold has been exceeded, the source network will be blocked out instead of just the offending host.
For a detailed discussion of how to specify threshold rules, see Section 7.9, Threshold Rules.
Manual Blocking and Exclude Lists
As a complement to threshold rules, it is also possible to manually define hosts and networks that are to be statically blocked or excluded. Manually blocked hosts and networks can be blocked by default or based on a schedule. It is also possible to specify which protocols and protocol port numbers are to be blocked.Exclude Lists can be created and used to exclude hosts from being blocked when a threshold rule limit is reached. Good practice includes adding to the list the firewall's interface IP or MAC address connecting towards the ZoneDefense switch. This prevents the firewall from being accidentally blocked out.
Example 7.12. Setting Up ZoneDefense
This example illustrates ZoneDefense setup where a host on a switch is blocked because a threshold rule for HTTP traffic triggers. It is assumed that all interfaces on the firewall have already been configured as shown below.
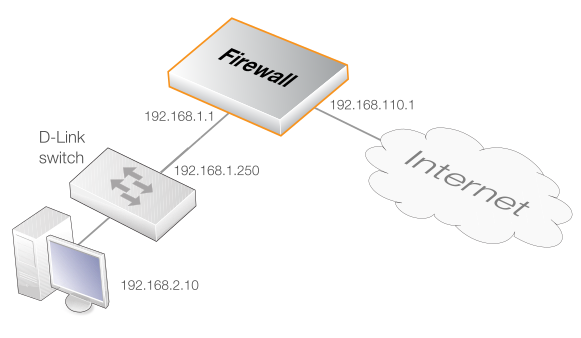
An HTTP threshold of 10 connections/second is to be applied to traffic. If the connection rate exceeds this, cOS Core will instruct the switch to block the host (within the network range 192.168.2.0/24).
A D-Link switch of model type DES-3226S is assumed, with a management interface address of 192.168.1.250 and it is connected to an interface with address 192.168.1.1. This interface will be added into the exclude list to prevent the firewall itself from being accidentally blocked by the switch.
InControl
Follow similar steps to those used for the Web Interface below.
Web Interface
Add a new switch into ZoneDefense section:
Add the firewall's management interface into the exclude list:
Configure an HTTP threshold of 10 connections/second:
Specify the threshold, the threshold type and the action to take if exceeded:
ZoneDefense with Anti-Virus Scanning
ZoneDefense can also be used in conjunction with the cOS Core Anti-Virus scanning feature. cOS Core can first identify a virus source through antivirus scanning and then block the source by communicating with switches configured to work with ZoneDefense.This feature can be activated via the following ALGs:
HTTP - ZoneDefense can block an HTTP server that is a virus source.
FTP - ZoneDefense can block a local FTP client that is uploading viruses.
SMTP - ZoneDefense can block a local SMTP client that is sending viruses with emails.
Anti-virus scanning with ZoneDefense is discussed further in Section 6.4.4, Anti-Virus with ZoneDefense and in the sections covering the individual ALGs. Configuring ZoneDefense with anti-virus scanning can be done with IP Policy objects by enabling it in a Anti-Virus Profile object that is then associated with a policy.
There are some differences in ZoneDefense operation depending on the switch model:The first difference is the latency between the triggering of a blocking rule to the moment when a switch actually starts blocking out the traffic matched by the rule. All switch models require a short period of latency time to implement blocking once the rule is triggered. Some models can activate blocking in less than a second while some models may require a minute or more.
A second difference is the maximum number of rules supported by different switches. Some switches support a maximum of 50 rules while others support up to 800 (usually, in order to block a host or network, one rule per switch port is needed). When this limit has been reached no more hosts or networks will be blocked out.
![[Important]](images/important.png) |
Important: Clearing the ACL rule set on the switch |
|---|---|
|
ZoneDefense uses a range in the ACL rule set on the switch. To avoid potential conflicts in these rules and guarantee the firewall's access control, it is strongly recommended that the administrator clear the entire ACL rule set on the switch before performing the ZoneDefense setup. |